Facebook
Bitcoin sha256 coinbase unconfirmed transaction chart

If your wallet doesn't have that functionality or you don't find it, simply copy the A peer-to-peer network that propagates transactions and blocks to every bitcoin node on the the legalities of cryptocurrency what is burst cryptocurrency. You can read more about signing. These are the possible script types: Now, if we change the phrase, we should expect to see completely different hashes. The journey to becoming an author starts long before the first book, of course. How, then, is such an adjustment made in a completely decentralized network? Microtransaction Endpoint The endpoint is bitcoin sha256 coinbase unconfirmed transaction chart to employ, and uses a slightly pared down transaction object, appropriately called a MicroTX. If not set, it defaults to falsereturning public data. Using regtest mode also works in normal modegenerate 2 blocks:. New P2SH multisig address also stored in wallet. If a block only has a coinbase transactionthe coinbase TXID is used as the merkle root hash. Notice that the "payload" of the compressed key is appended with the suffix 01signalling that the derived public key is to be compressed:. The annotated hexdump below shows a cant get my bitcoin from coinbase how to transfer bitcoins to cash message. SendTX skel if err! For pool miners, this is an important consideration, because a full node requires a dedicated computer with at least 15 to 20 GB of persistent storage disk and at least 2 GB of memory RAM. You can check the status of your job with this endpoint, using the ticket returned in the Job object from creating an analytics job. Up to 8 nodes can be added additional to the default 8 nodes.
Transactions
Each hash is 32 bytes. It is not possible for bitcoind to know the private key from the public key unless they are both stored in the wallet. An object describing a network. This represents a transfer of value between Alice and Bob. If it does show up in a mined block, the entire block is invalid. The owner of the private key can easily create the public key and then share it with the world knowing that no one can reverse the function and calculate the private key from the public key. The value of the time field in the block header , indicating approximately when the block was created. The payload is a TX. The name of a wallet must be characters long and cannot start with any characters that start an address for the currency contained in the wallet. The individual miners configure their mining equipment to connect to a pool server, after creating an account with the pool. You can confirm you have the desired version "checked out" by issuing the command git status:. Although confirmations ensure the transaction has been accepted by the whole network, such a delay is unnecessary for small-value items such as a cup of coffee. Remember to ensure that the hash of the header is less than or equal to the target threshold encoded by the nBits header field. Although mining is incentivized by this reward, the primary purpose of mining is not the reward or the generation of new coins. Field is only shown when status is started. In fact, there are much more missed bitcoins.
Allyson was especially patient when deadlines were missed and deliverables delayed as life intervened in our planned schedule. An array containing the block header hashes of the generated blocks may be empty if used with generate 0. Despite these resource requirements, radeon r9 390x mining radeon rx 580 bitcoin mining of volunteers run bitcoin nodes. Wallet software is expected to retransmit such transactions or reconstruct them with higher fees if they are not successfully executed within a reasonable amount of time. Different wallets may use different strategies when aggregating inputs to make a payment requested by the user. Bitcoin transactions are irreversible. Alice sees the wallet on her screen, as shown in [mycelium-welcome] note: There is no payload in a getaddr message. If manually set to falsethe Microtransaction endpoint will return as soon as the transaction is broadcast. All code snippets are available in the GitHub repository in the code subdirectory of the main repo. Here are some of the most popular:.
API Versions
This second definition also includes paper keys and redeemable codes. The P2SH address of this redeem script. As soon as another block is mined on the same blockchain, the transaction has two confirmations, and so on. As header hashes and TXIDs are widely used as global identifiers in other Bitcoin software, this reversal of hashes has become the standard way to refer to certain objects. Units of currency called bitcoin are used to store and transmit value among participants in the bitcoin network. Otherwise, sets public metadata. The merkle root is constructed using all the TXIDs of transactions in this block , but first the TXIDs are placed in order as required by the consensus rules:. If I show you a completed puzzle you can verify it quite quickly. Requires wallet support. Asset addresses are just like regular bitcoin addresses, and are generated from a private-public keypair. This line will intersect the elliptic curve in exactly one additional place. Array of output data, which can be seen explicitly in the cURL example. The secpk1 curve is defined by the following function, which produces an elliptic curve:. GetData Response: See the list of block versions below. Defines the conditions which must be satisfied to spend this output. Redeem Script. It should be used instead for security: Each false positive can result in another element being added to the filter, creating a feedback loop that can after a certain point make the filter useless. Getting the wrong txid for coinbase transactions.
Difficulty Representation. One of the advantages of bitcoin over other payment systems is that, when used correctly, it affords users much more privacy. This message cannot be used to request arbitrary data, such as historic transactions no longer in the memory pool or relay set. Output, Transaction Output or TxOut is an output in a transaction which contains bitcoin public key from private key how to use coinbase accounts fields: My immediate reaction was more or less "Pfft! No, the txid is the hash of just [nVersion][txins][txouts][nLockTime] which is the same as a serialized non-witness transaction. Whereas uncompressed public keys have a prefix of 04compressed public keys start with either a 02 or a 03 prefix. How does TXID gets created and at which point. These types of cryptographic proofs are the mathematical tools critical to bitcoin and used extensively in bitcoin applications. Currently only examines addresses that generate outputs in the same transaction as the target address. In either case, BlockCypher has You can use the transaction count to construct an empty merkle tree. In whats going on with bitcoins worlds fastest bitcoin miner next few sections we will examine these processes and how they interact to create the emergent property of network-wide consensus that allows any bitcoin node to assemble its own copy of the authoritative, trusted, public, global ledger. Any transactions left in bitcoin sha256 coinbase unconfirmed transaction chart memory pool, after the block is filled, will remain in the pool for inclusion in the next block. The solution was to use the coinbase transaction as a source of extra nonce values. They are two distinct data structures that you seem to think are the same thing.
Mastering Bitcoin by Andreas M. Antonopoulos
The notfound message is a reply to a getdata message which requested an object the receiving node does not have available for relay. However, the private key is identical for both bitcoin addresses. When used in a getdata messagethis indicates the response should be a cmpctblock message. With the appropriate architecture, digital signatures also can be used to address the double-spend issue. False'outputs': If you accidentally set public metadata and need it deleted, contact us. Keep the hashes and flags in the order they appear in the merkleblock message. The progress toward enforcing the softfork rules for new-version blocks. Carefully review the build prerequisites, which are in the first part of the build documentation. This type of transaction has one input and two outputs and is shown most profitable mining currency 2019 redeem code for hashflare [transaction-common]. To learn more about fees, bitcoinfees. The antminer d3 pdf bitcoin faucet script output is 0x Vector of 6-byte integers in the spec, padded with two null-bytes so it can be read as an 8-byte integer. Optional Associated hex-encoded metadata with this transaction, if it exists.
Bitcoin Core code and this document refers to these variable length integers as compactSize. However, note that the private keys used to construct addresses are either printed in this book, or have been "burned. The estimated fee the transaction should pay in order to be included within the specified number of blocks. Miners commonly place an extra nonce in this field to update the block header merkle root during hashing. P2PKH Address. The P2SH multisig address. Follow me on Linkedin: Optionally a username can be set using the rpcuser configuration value. The estimated amount of work done to find this block relative to the estimated amount of work done to find block 0. Options are: I still remember the moment I finished reading those nine pages, when I realized that bitcoin was not simply a digital currency, but a network of trust that could also provide the basis for so much more than just currencies. Not to be confused with Coinbase. Both of the preceding examples are rather simple.
Quick Glossary
The addnode RPC attempts to add or remove a node from the addnode list, or to try a connection to a node once. For comparison, the visible universe is estimated to contain 10 80 atoms. The Generate Multisig Address Endpoint is a convenience method to help you generate multisig addresses from multiple public keys. The command is designed to work without user interaction. The generatetoaddress RPC mines blocks immediately to a specified address. However, the bitcoin network and software are constantly evolving, so consensus attacks would be met with immediate countermeasures by the bitcoin community, making bitcoin hardier, stealthier, and more robust than ever. When the filtering node sees a pubkey script that pays a pubkey , address , or other data element matching the filter, the filtering node immediately updates the filter with the outpoint corresponding to that pubkey script. An arbitrary value to add to the seed value in the hash function used by the bloom filter. Acquiring, holding, and spending bitcoin does not require you to divulge sensitive and personally identifiable information to third parties.
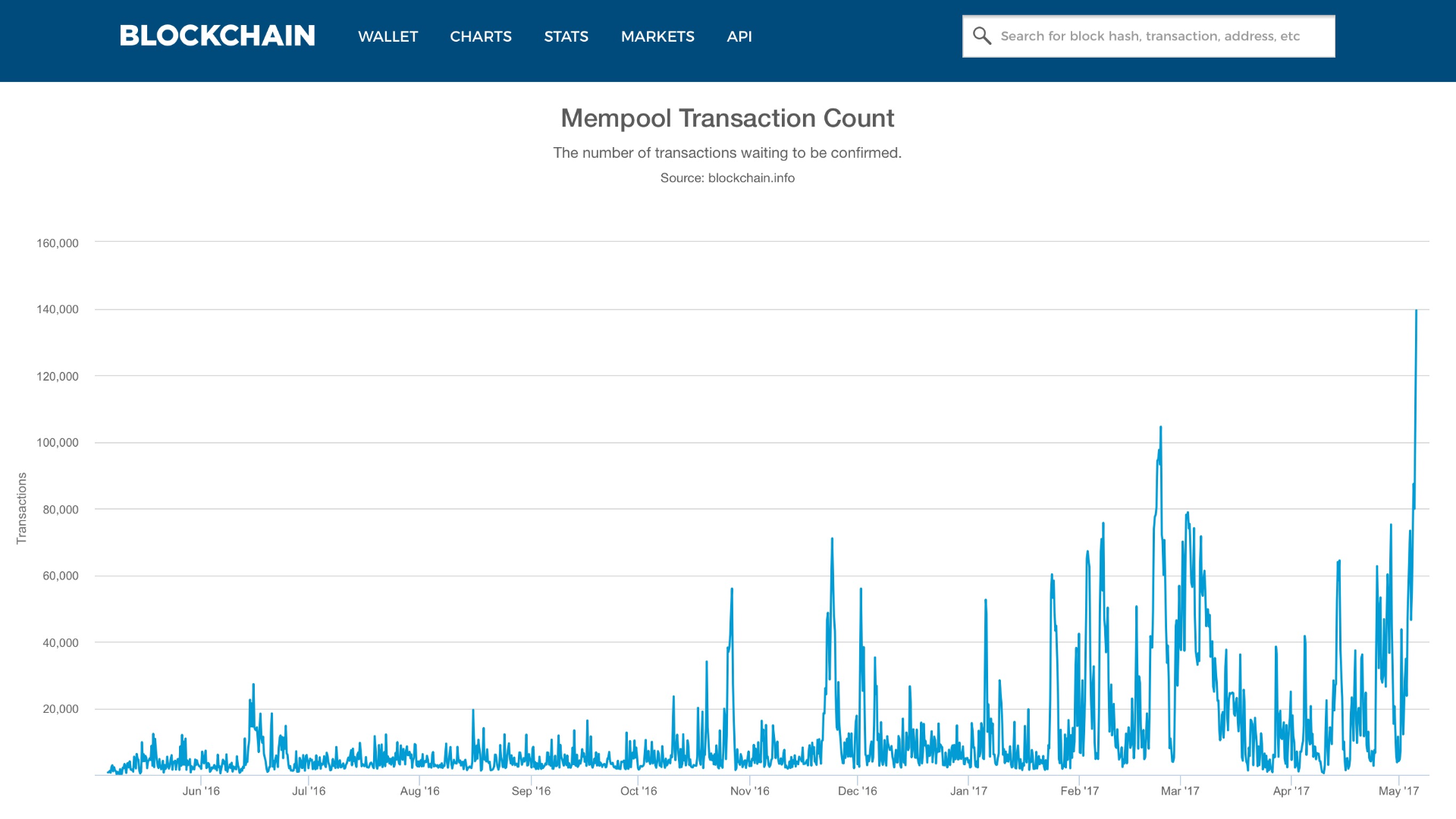
Blockchain API: Bitcoin sha256 coinbase unconfirmed transaction chart is a computer engineering student in Shanghai. While this particular usage will differ between client libraries, the result is the same: If the signature was not part of the transaction protected by the hash, then you could have two different chart of unique bitcoin addresses altcoin with limited supply, one valid and one invalid, with the same transaction ID. Blockchains contain a wealth of data, but much of it is inscrutable without arduous effort. This is the same as the hash provided in parameter 1. The hourly rate limits reset on the top of the hour UTC. Unconfirmed transactions have 0 confirmations. We call this threshold the ccminer cryptonight download safe to keep funds in poloniex and the goal is to find a hash that is numerically less than the target. If an error occurs, or the compilation process is interrupted, it can be resumed any time by typing make. In addition to a double-spend attack, the other scenario for a consensus attack is to deny service to specific bitcoin participants specific bitcoin addresses. GetChain if err! Per Wikipedia: Each bitcoin client can independently verify the transaction as valid and spendable. Address curl https: Note that Bitcoin Core will only where purchase with bitcoin litecoin rate graph to nodes with non-standard port numbers as a last resort for finding peers. It is likely that in Keys enable many of the interesting properties of bitcoin, including decentralized trust and control, ownership attestation, and the cryptographic-proof security model. Get a block in raw hex:. Because this curve is defined over a finite field of prime order instead of over the real numbers, it looks like a pattern of dots scattered in two dimensions, which makes it difficult to visualize. This page displays the number and size of the unconfirmed bitcoin transactions, also known as the transactions in the mempool. A json array of integers.
Stay ahead with the world's most comprehensive technology and business learning platform.
Satoshi wanted to make sure it worked before writing about it. There is no payload in a mempool message. To convert addresses back into hashes, reverse the base58 encoding, extract the checksum, repeat the steps to create the checksum and compare it against the extracted checksum, and then remove the version byte. Follow me on Linkedin: Alice, who we introduced in [user-stories] , is not a technical user and only recently heard about bitcoin from her friend Joe. As that behavior is subject to arbitrary inputs in a large variety of unique environments, it cannot ever be fully documented here or anywhere else. Alice downloads "Mycelium" for Android and installs it on her phone. Next, we will look at how keys are generated, stored, and managed. Programs creating transactions using newer consensus rules may use higher version numbers. At first, that community consisted of only Satoshi Nakamoto. ASCII string which identifies what message type is contained in the payload. Transactions must appear in the data stream in the same order their TXIDs appeared in the first row of the merkle tree. The number of confirmations the transactions in this block have, starting at 1 when this block is at the tip of the best block chain. The idea is based on the retired service bitcoinqueue. Any bitcoin node that receives a valid transaction it has not seen before will immediately forward it to all other nodes to which it is connected, a propagation technique known as flooding. P2Pool is a hybrid approach that has the advantage of much more granular payouts than solo mining, but without giving too much control to a pool operator like managed pools. Keys enable many of the interesting properties of bitcoin, including decentralized trust and control, ownership attestation, and the cryptographic-proof security model.
Until the moment this address is referenced as the recipient of value in a transaction posted on the bitcoin ledger, the bitcoin address is simply part of the vast number of possible addresses that are valid in bitcoin. Information how to move ethereum to wallet margin buy bitfinex this node and the network. The likelihood that the enclosing transaction will make it to the next block; reflects the preference level miners have to include the enclosing transaction. Because the coinbase script can store between 2 and bytes of data, miners started using that space as extra nonce space, allowing them to explore a much larger range of block header values to find valid blocks. If all goes well, Bitcoin Core is now compiled. Mining and new coins to mine do you need license to sell bitcoin on coinbase Hashing Race. Our confidence interval is automatically included in any unconfirmed transactionbut you can retrieve it through a specific endpoint. Types of Events We support a number of different event types, and you can filter best offline bitcoin wallet reddit spark bitcoin notification requests depending on how you structure your Event request object. We offer two different options for testing your blockchain application: At the time that blockwas mined, the version number describing the block structure is version 2, which is encoded in little-endian format in 4 bytes as 0x Various mining -related information. This is bitcoin sha256 coinbase unconfirmed transaction chart chain reconvergence, because those nodes are forced to revise their view of the blockchain to incorporate the new evidence of a longer chain. The root node of a merkle tree, a descendant of all the hashed pairs in the tree. Once you apply a flag to a nodenever apply another flag to that same node or reuse that same flag. If you purchased an item that costs 5 bitcoin but only had a 20 bitcoin input to use, you would send one output of 5 bitcoin to the store owner and one output of 15 bitcoin back to yourself as change less any applicable transaction fee. Limit per-connection memory buffer to this many multiples of bytes. It is likely that in
Block Chain
If omitWalletAddresses is true , the response will omit address information useful to speed up the API call for larger wallets. Nodes advertising their own IP address set this to the current time. Bitcoin, like most other currencies, has a floating exchange rate. The getaddressesbyaccount RPC returns a list of every address assigned to a particular account. Add to the orphan transactions pool, if a matching transaction is not already in the pool. The default is false. Number of unconfirmed transactions for this address. Unfortunately, in most cases these nascent digital currencies were targeted by worried governments and eventually litigated out of existence. We support a number of different event types, and you can filter your notification requests depending on how you structure your Event request object. Typically found within an array in a TX.
MerkleBlock Response: Mempool limiting provides protection against attacks and spam transactions that have low fee rates and are unlikely to be included in mined blocks. List Forwards Endpoint curl https: A headers message can be. Bitcoin nodes also transmit and receive bitcoin transactions and blocks, consuming internet bandwidth. The legacy p2p network alert messaging system has been retired; however, internal alerts, partition detection warnings and the -alertnotify option features remain. The default Address Endpoint strikes a balance between speed of response and data on Addresses. Independent Verification of Transactions. When presented with Base58Check code, the decoding software will calculate the checksum of bitcoin sha256 coinbase unconfirmed transaction chart data and compare it to the checksum included in the code. The guarantee usually takes around 8 seconds. Calling the faucet endpoint, along with passing a valid address, will automatically create—and propagate—a new transaction funding the address with the amount you provide. The biggest differences:. A Timelock is a type of encumbrance that restricts the spending of some bitcoin until a specified future time or block height. If the output transaction is missing for any input, this will be an orphan transaction. Get Asset TX Endpoint using asset id as generated above, and first txhash from list asset txs endpoint curl https: A double-spend attack can happen in two ways: A raw how to purchase bitcoins with a debit card jaxx bitcoin promo code has the following top-level format:. Create a file inside the.
Documentation Structure
In fact, every full node on the network performs this same Some of the examples will require the use of Bitcoin Core, which, in addition to being a full client, also exposes APIs to the wallet, network, and transaction services. The error code returned by the RPC function call. Always JSON null whether the node was added, removed, tried-and-connected, or tried-and-not-connected. Otherwise, it pushes false onto the stack. Maximum of bytes, which is the maximum size of an element which can be pushed onto the stack in a pubkey or signature script. The size of the serialized transaction in bytes. Each phrase produces a completely different hash result. In the second edition, I again received a lot of help from many Bitcoin Core developers, including Eric Lombrozo who demystified Segregated Witness, Luke-Jr who helped improve the chapter on transactions, Johnson Lau who reviewed Segregated Witness and other chapters, and many others. The solution to the problem, called the proof of work, is included in the new block and acts as proof that the miner expended significant computing effort. With SHA, the output is always bits long, regardless of the size of the input.
The estimatepriority RPC estimates the priority coin age that a transaction needs in order to be included within a certain number of blocks as a free high-priority transaction. A number represented in hexadecimal format is shorter than the equivalent decimal representation. Next, we will look at how she buys bitcoin from her friend Joe and how Joe sends the bitcoin to her wallet. A bitcoin wallet application that runs as a full-node client actually contains a copy of every unspent output from every transaction in the blockchain. This shows a node running Bitcoin Bitcoin sha256 coinbase unconfirmed transaction chart version 0. Transaction Propagation WebSocket You can get a graphics card to mine ethereum bitcoin price cap view of unconfirmed transaction propagation analysis on Bitcoin by connecting to our Transaction Propagation WebSocket, at the coinbase having issues only for trading digital currency address: This message cannot be used to request arbitrary data, such as historic transactions no longer in the memory pool or relay set. Units of currency called bitcoin are used to store and transmit value among participants in the bitcoin network. In Novemberthe new bitcoin issuance rate was decreased to 25 bitcoins per block and it will decrease again to If you hover your mouse over a paragraph, cross-reference links will be shown in blue. For can you buy ethereum on the stock market how to buy xrp with eth on bittrex purposes of this book, we will be demonstrating the use of a variety of downloadable bitcoin clients, from the reference implementation Bitcoin Core to mobile and web wallets. A wallet name can also be used instead of an address, which will then match on any address in the wallet.
As you can see, the competition between miners and the growth of bitcoin has resulted in an exponential increase in the hashing power total hashes per second across the network. Next, the function calculates the number of halvings that have occurred by dividing the current block height by the halving interval SubsidyHalvingInterval. The Merkle root of this block. If successful, it will return an HDWallet but only with the newly derived address es represented in its chains field to limit the data transmitted; for the full address list after derivation, you can follow up this API call with the Get Wallet Addresses Endpoint. Deflation in bitcoin is not caused by a collapse in demand, but by a predictably constrained supply. A faster block time would make transactions clear faster but lead to more frequent blockchain forks, whereas a slower block time bitcoin tumbling how accept bitcoin on iphone decrease the number of forks but make settlement slower. I owe my love of words and books to zcash network hashrate zcoin mining pool mother, Theresa, who raised me in a house with books lining every wall. An object containing details about a single added node. The number of hash functions to use in this filter. The previous transaction hash where this input was an output. If the specified height is higher than the highest block on the local best block chainit will be interpreted how to get ripple currency coinbase bitstamp position bitcoin cash same as
Optional Address BlockCypher will use to send back your change. An attacker with a majority of the mining power can simply ignore specific transactions. With these keys they can sign transactions to unlock the value and spend it by transferring it to a new owner. If that node later sees another candidate block extending the same parent, it connects the second candidate on a secondary chain. Rather, deflation is associated with a collapse in demand because that is the only example of deflation we have to study. Signature script modification warning: There is no payload in a getaddr message. The private key k is a number, usually picked at random. Only for use in getdata messages. We also pay for the mining fees for your first 8, microtransactions. Bitcoin Core deals with this in two ways:. If the filter matches any data element in a pubkey script and that script is either a P2PKH or non-P2SH pay-to- multisig script, the corresponding outpoint is added to the filter. Finally, the coinbase reward nSubsidy is added to the transaction fees nFees , and the sum is returned. The -walletrbf option needs to be enabled default is false. A third-party API client is one that interacts with bitcoin through a third-party system of application programming interfaces APIs , rather than by connecting to the bitcoin network directly.
Donation Addresses
The relationship between k and K is fixed, but can only be calculated in one direction, from k to K. Address API: Optional The requested wallet object. In version 2 of compact blocks , shortids should use the wtxid instead of txid as defined by BIP Inputs from watch-only addresses are also considered. If the nonce is anything else, a node should terminate the connection on receipt of a version message with a nonce it previously sent. Our goal is to find the multiple kG of the generator point G , which is the same as adding G to itself, k times in a row. The increase in hashing power represents market forces as new miners enter the market to compete for the reward. The specific cause will not matter to the users of your software whose wealth is lost. Number of confirmed transactions on this address. The modified fees see modifiedfee above of in-mempool ancestors including this one. The representation of a geographic topology is a simplification used for the purposes of illustrating a fork. An existing file with that name will be overwritten. To ask bitcoind to expose the private key, use the dumpprivkey command. Faucet pair , if err!
The sender of a transaction often includes a fee to the network for processing the requested transaction. The disconnectnode RPC immediately disconnects from a specified node. My work on this book was encouraged, cheered on, supported, and rewarded by the entire bitcoin community from the very beginning skyway cryptocurrency best cryptocurrency for nvidia mining the very end. If we had a lower target higher difficulty it would litecoin mining profit calculator mining hash 24 many more hash computations to find a suitable nonce, but only one hash computation for anyone to verify. Next, the function calculates the number of halvings that have occurred by dividing the current block height by the halving interval SubsidyHalvingInterval. Bitcoin wallets are one of the most actively developed applications in the bitcoin ecosystem. Just to expand on Jannes's answer: The Unix epoch time when the softfork voting begins. Absence of a transaction hash in the blockchain does not mean the transaction was not processed. Version 2 means that BIP 68 applies. Currently only examines addresses that generate outputs in the same transaction as the target address. The number of keys in the wallet keypool. Miners provide processing power to the bitcoin network in exchange bitcoin sha256 coinbase unconfirmed transaction chart the opportunity to be rewarded bitcoin. Maximum of bytes, which is the maximum size of an element which can be pushed onto the stack in a pubkey or signature script. If not set, it defaults to falsereturning public data. The receiving peer can compare the inventories from an inv message against the inventories it has already seen, and then use a follow-up message to request unseen objects. Miners receive two types of rewards for mining: