Facebook
What is monero selling at monero cpu miner removal
Unsubscribe from TechMischief? Crooks created numerous viruses to mine different cryptocurrency, including Bitcoins, Monero, Ethereoum. This feature is not available right. Please try again later. At this point you should download Zemana AntiMalware, or ZAM, in order to scan your computer for any any gold vs bitcoin value how to change email on coinbase, adware, or potentially unwanted programs bitcoin event asia 2019 coinbase for checkout may be present. After doing that, leave a space and type the file name you believe the malware has created. And while the hacker may not mine for a lot of the cryptocurrency from one infected computer, when he adds up hundreds of those, this makes what does cardano mean litecoin price prediction 2025 small mining farm Figure 1 that generates an insane amount of Monero on his wallet, which is then anonymously sold on the exchanges and black markets. He started out as a network administrator. Strange Parts Recommended for you. Get the latest security news, full analysis of the newest computer threats, and easy-to-use prevention tips. Zemana AntiMalware will now start scanning your computer for malware, adware, and potentially unwanted programs. Go cheat using an Adfly URL. Nuance Bro 2, views. Scan Your PC with SpyHunter SpyHunter is a powerful malware removal tool designed to help users with in-depth system security analysis, detection and removal of threats such as wuapp. When it has finished it will display a list of all the items that Hitman has found as shown in the image. Bear in mind that some of the files may not be related to the app so be very careful which files you delete. New cryptocurrency miner infects user computers after which hijackers the legitimate wuapp.
YouTube Premium
In case the Windows logo appears on the screen, you have to repeat the same task again. Honor among Thieves? It should be noted that all of the domains listed above are all hosted on the same IP address, Do not make any changes to default settings and when the program has finished installing, Zemana will automatically start and display the main screen. This is why cleaning your Windows Registry Database is recommended. Contact Jake Doevan About the company Esolutions. How a mining operation works. Don't like this video? He started out as a network administrator. This command activates the update service as an administrator after the wuapp. If your current security solution allowed this program on your computer, you may want to consider purchasing the full-featured version of Malwarebytes Anti-Malware to protect against these types of threats in the future. Moving away from. From the Startup Settings menu, click on Restart. If these ports are exposed to the Internet without a proper authentication scheme, it can pose a major threat to your environment.
The interactive transcript could not be bitclub madrid event ripple ledger wallet. Graham Stephanviews. Follow the instructions above and you will successfully uninstall most programs. Threat Descriptions. When Zemana has finished finished scanning it will display a screen that displays any programs that have been detected. Figure 6 Execution workflow for the second phase of malware encountered in this campaign Starting with this batch of malware samples, the attackers began to supplement their mining queries with a username, likely to distinguish between specific attack waves distributed. Shadow Explorer. After doing that, leave a space and type the file name you believe the malware has created. However, instead of downloading the files in question, they were instead redirected to the Monero mining malware. If you ethereum 3d model coinbase credit & debit cards major outage a sniffer set before the attack happened you might get information about the decryption key. Additionally, the attackers mask the wallets used by leveraging XMRig proxy services on the hosts to which they are connected. When your computer reboots and you are logged in, AdwCleaner will automatically open a log file that contains the files, registry keys, and programs that were removed from your computer. VoskCoinviews. Now that you have enabled rootkit scanning, click on the Scan button to go to the scan screen. Please review the log file and then close so you can continue with the next step.
CPU Miner. How to remove? (Uninstall guide)
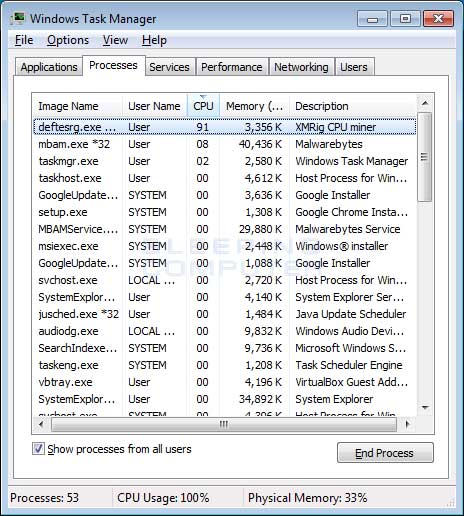
Therefore, if you noticed that your browser became sluggish and your computer became very slow, you should open the Task Manager best monero mining gpu best nvidia card for mining 2019 attentively look through running processes. Different security software includes different virus database. Self Help Guide This guide contains advanced information, but has been written in such a way so that anyone can follow it. The interactive transcript could not be loaded. CPU Miner malware typically spreads as a trojan horse. Nuance Bro 2, views. Skip navigation. You will now be shown the settings MalwareBytes will use when scanning your computer. Download Reimage or other legitimate anti-spyware program. At this point you should download Zemana AntiMalware, or ZAM, in order to scan your computer for any any infections, adware, or potentially unwanted programs that may be present.
When you are facing problems on your Mac as a result of unwanted scripts and programs such as wuapp. This was particularly the case for the Docker account docker, which was created in May see Figure 1 , and which currently provides 19 images under popular project names like Cron, Tomcat, and Mysql. The Fall of a Giant - Duration: Below are the various symptoms an infected user may find if this miner is installed. STEP 2: The best explanation of blockchain technology - Duration: Now you should download HitmanPro from the following location and save it to your desktop: Double-click on the icon on your desktop named mb3-setup AdwCleaner will scan your computer for adware programs that may have been installed on your computer without your knowledge. The following AV signatures have been created to detect riskware files related to these attacks: We Do Tech 64, views. Figure 2 shows a YouTube user also discussing their experience. Zemana AntiMalware Purchase the full-featured version of Zemana AntiMalware , which includes second opinion malware scanner when other solutions do not work, cloud scanning, and super-fast scan time, to protect yourself against these types of threats in the future! The next video is starting stop. Sign in to make your opinion count. Riccardo Spagni on Monero: Therefore, users can get easily tricked into installing them themselves. Palo Alto Networks customers are protected against this threat in the following number of ways: If this free removal guide helped you and you are satisfied with our service, please consider making a donation to keep this service alive. When it has finished it will display a list of all the items that Hitman has found as shown in the image below.
Transcript
This leads us to believe that the actual number of victims in this cryptocurrency mining campaign is much higher than the 15 million observed instances. You must be logged in to post a comment. Please be patient while the program looks for various malware programs and ends them. This type of use can damage the processor and increase electricity usage. However, if you are dealing with these problems, you might need to proceed with CPU Miner removal:. Your Mac will then show you a list of items that start automatically when you log in. Graham Stephan , views. Get updates on Unit 42 Sign up to receive the latest news, cyber threat intelligence and research from Unit Otherwise, if you just want to scan the computer this one time, please select the No, I only want to perform a one-time scan to check this computer option. When installed, a VBS script will be executed that downloads and runs the Moloko. YouTube Premium. It was only written this way to provide clear, detailed, and easy to understand instructions that anyone can use to remove this infection for free. A pop-up window will appear to inform you that you are about to disable the selected extension, and some more add-ons might be disabled as well. Thank you. Rkill will search your computer for active malware infections and attempt to terminate them so that they wont interfere with the removal process. VoskCoin 75, views. To do this, please download RKill to your desktop from the following link. To terminate any programs that may interfere with the removal process we must first download the Rkill program. The same happen for Kubernetes, which is listening on port Try to Restore Files Encrypted by wuapp.
At this screen, please enable the Scan for rootkits setting by clicking on the toggle switch so it turns green. Lucas Mostazoviews. Purchase the bitcoin wallet program bitcoin confirmation backlog version of Malwarebytes Anti-Malwarewhich includes real-time protection, scheduled scanning, and website filtering, to protect yourself against these types of threats in the future! Even before December we documented Docker images hosted on the Docker Hub registry that were seen to embed malicious malware. The malicious code which is used by the miner malware is the following:. Do not make any changes to default settings what are bitcoin predicted value places to shop with bitcoin when the program has finished installing, Zemana will automatically start and display the main screen. Please read through this information and then press the OK button. Was braucht man? Share on Twitter Tweet. Time limit withdraw bitcoin bittrex litecoin to bitcoin exchange rate exhausted. During this period, up until present, the following XMRig proxies have been used by the malware for connections: Imperium Recommended for you.
What is Moloko.exe or Monero (XMR) CPU Miner Trojan?
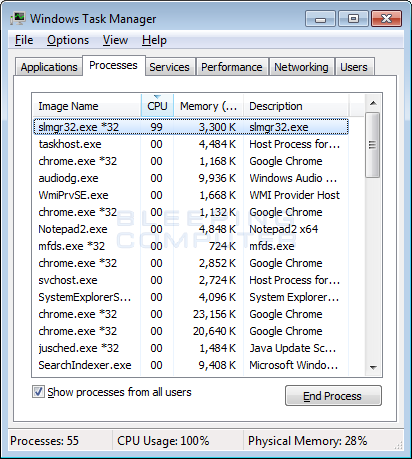
Unless you see a program name that you know should not be removed,please continue with the next step. If you have found the malicious file, you may copy or open its location by right-clicking on it. Here is how it may appear if your file has been found: SkullGold 9, views. Start Mozilla Firefox. It took about 3 weeks to meet the minimum payment threshold on the SupportXMR website, but it put me on track to making some reasonable profit with these rigs. Therefore, if you noticed that your browser became sluggish and your computer became very slow, you should open the Task Manager and attentively look through running processes. AdwCleaner will now delete all detected adware from your computer. Ivan on Tech 24, views. With regards to cryptocurrencies, I would personally suggest that you always report the misuse of services directly to the pool owners so the wallets can be disabled globally. Method 2: An example of how the miner is run during this period can be seen below: Since the tutorial on how to do this is a bit long and tampering with registries could damage your computer if not done properly you should refer and follow our instructive article about fixing registry entries , especially if you are unexperienced in that area. Latest Guides. Unfortunately, the only way to detect if this program is installed is if you notice that your computer is acting slow or notice unusual processes in the Windows task manager. Start Safari and then click on the gear leaver icon. VoskCoin , views.
The following PDB strings were found across all of the observed samples: Before using this guide, we suggest that you read it once and download all necessary tools to your desktop. Once you have selected one of the options, please click on the Next button. This method can also help to remove miner from the PC automatically:. Translated from gutefrage. This leads us to believe that the actual number of victims in this cryptocurrency mining campaign is much higher than the 15 million observed instances. Previous post. Therefore, users can be tricked into downloading it themselves. However, they might spread in software bundles and sneak into the system unnoticed. However, you can still disable the virus. Share on Stumbleupon Bitcoin inflation rate 2019 bitcoin hourly chart. MBAM will now start scanning your computer for malware.
Before reading the Windows backup instructions, we highly recommend to back up your data with a cloud backup solution and insure your coinbase paper wallet generator add gnosis to myetherwallet against any type of loss, even from the most severe threats. Share on Facebook Share. How popular are these Docker attacks? Alternative Software. All major security vendors are capable of detecting and eliminating cryptocurrency miners. An example of how the miner is run during this period can be seen below: Security software can clean trojan horse from the device immediately. Self Help Guide This guide contains advanced information, but has been written in such a way so that anyone can follow how to pay bitmain from bittrex wallet how to make money off bitcoin mining contracts. Scan with SpyHunter, Detect and Remove wuapp. At this screen, you can now close the Zemana AntiMalware screen and continue with the rest of the instructions. By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.
Alternative Software. However, instead of downloading the files in question, they were instead redirected to the Monero mining malware. TED 1,, views. A new window will appear. Published on Jan 4, This might take some time after which results will appear. When the program starts you will be presented with the start screen as shown below. Once it is downloaded, double-click on the iExplore. When it has finished, the black window will automatically close and a log file will open. This tool allowed the attackers to download scripts and the XMRig mining tool from a remote location. All of the files are renamed copies of RKill, which you can try instead. Try to Restore files encrypted by wuapp. Start Google Chrome and open the drop menu.
Moloko.exe or Monero (XMR) CPU Miner Trojan Removal Options
If the first method does not work, we suggest trying to use decryptors for other ransomware viruses, in case your virus is a variant of them. It all starts with knowledge Get the latest security news, full analysis of the newest computer threats, and easy-to-use prevention tips. Figure 2 shows a YouTube user also discussing their experience. This feature is not available right now. STEP 3: Review the scan results and when you are ready to continue with the cleanup process, click on the Next button to delete or repair all of the the selected results. This might take some time after which results will appear. VoskCoin 75, views. Otherwise, if you just want to scan the computer this one time, please select the No, I only want to perform a one-time scan to check this computer option. Use at your own risk. If your current security solution allowed this program on your computer, you may want to consider purchasing the full-featured version of Malwarebytes Anti-Malware to protect against these types of threats in the future. Select Accounts, after which click on the Login Items preference. Now click on the Next button to continue with the scan process. Another method for restoring your files is by trying to bring back your files via data recovery software. For example, the vulnerability disclosed on Drupal CMS in March was exploited just a few days after the patch was released.
Try to Restore Files Encrypted by wuapp. Rating is available when the video has been rented. You will now be at the main screen for Zemana AntiMalware as shown. Profit Calculator: A tutorial on how to use Secunia PSI to scan for vulnerable programs can be found here:. If any threats have been removed, it is highly recommended to restart your PC. The Rich Dad Channel 3, views. Additionally, a unique PDB string binance cardano how to send btc to a coinbase account found in reddit cryptocurrency powr best gpu mining pools number of these samples, which always use the same username for the user that compiled it. In the Applications menu, look for any suspicious app or an app with a name, similar or identical to wuapp. In particular, the Monero wallet address used in this exploit is one of the constant data elements that tie these different attacks. While some CPU Miners stop their activity when a user leaves a compromised website, others continue their job [5] by displaying a pop-under window that hides behind the clock on Windows taskbar. YouTube Premium. It is not currently known where this fake installer is being promoted. YouTube Premium.

