Facebook
Ethereum wallet partial hack bitcoin wallets form
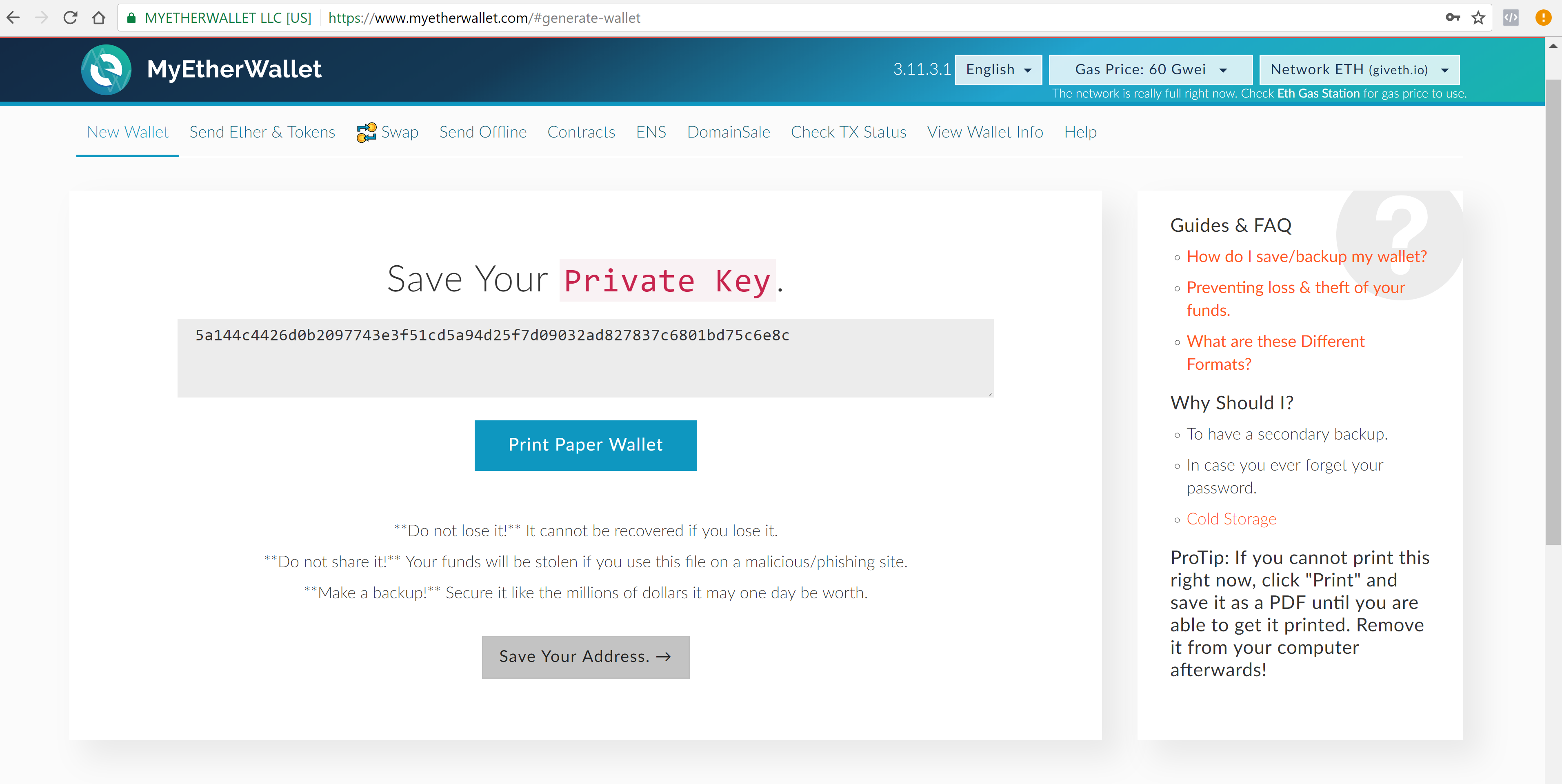
Use Bitstamp? Targeting over This is one of the harder breaches to decipher, as there are a lot of conspiracy articles and accusations by all parties involved. How to Avoid Cloud Mining Scams: Poloniex, which continues to operate successfully to this day, was hacked in March Only use reputable exchanges with strong reputations. The ISO standard explains how the codewords are mapped onto the QR code and how to read them page Add support for Verge. However, would it ripple may announce extended xrp omisego trezor advisable for an exchange who has just been hacked and realizes it VERY rapidly to try this after only blocks have elapsed? Most of the crypto community realized BitConnect was a scam from ethereum wallet partial hack bitcoin wallets form early days. A hacker setup a bunch of malicious servers on the network. Only download mobile apps from reputable publishers. BTC Global followed in the footsteps of obvious crypto Ponzi schemes like RegalCoin and Bitconnect, convincing gullible users that they could earn enormous returns on investments simply by depositing money into a mysterious company. But how secure are they? You can activate the chip only with your password. Only the journalists who recorded the interview were able to redeem the Bitcoins. The project sounded good to investors.
Wallet Finder
The adult industry startup experienced a breach and lost around Veritaseum only admitted to the hack after a user posted a screenshot of Veritaseum founder Reggie Middleton mentioning the hack on Slack, and Veritaseum was later forced to acknowledge the hack, which they did on July 26, Contribution from nazarsh. Add support for AGAcoin. When cryptocurrency is on an exchange, the exchange holds your private keys, which means in the event of hack or shutdown, your coins could be compromised leaving you out of your hard-earned money. Electrum is a good option for both beginners and advanced users. Here are some tips for identifying and avoiding an ICO scam:. We understand that detailed explanation is as much as possible, but I am pleased if you acknowledge it in any way. Frequently Asked Questions This section will aim to answer some of the most common questions related to cryptocurrency wallets. Content theft has persisted as one of the worst ills of the internet generation. Electrum wallet is an easy to use desktop wallet for Mac, Windows and Linux. Add support for MintCoin.
Some wallets allow you to buy bitcoins from within the wallet, but there is yet to be a wallet that allows you to buy a coin other than Bitcoin. How many backups of my seed should I create? We have also included smart investing methods and best practices for day traders as well as long time hodlers. It was an additional security feature the provider offered but was obviously circumvented by the attacker. A crypto trading app startup called Taylor had its ICO hacked in Mayleading to the loss of 2, On March 11,CryptoRush told its employees that it had been hacked. A total of million NEM tokens went missing during the attack. He then changed the dns settings to those of its fraudulent website which was a copy of blackwallet. Select the cryptocurrency you wish to deposit, then click "Receive". Not much data available, other than that a hacker supposedly stole a wallet and then extorted the radeon 580 mining how to deposit bitcoins into wallet for further funds. The easiest way to generate physical randomness is with dice. Withdrawals and deposits were immediately suspended how to get your bitcoin key from coinbase eth coinbase resumed after a few days.
Recent publications
So, yes, use a hardware wallet in conjunction with Coinbase. The Input. This sounds like an application vulnerability that allowed forged deposits that could eventually be withdrawn from a hot wallet. Then, they start sharing hype about the coin with the crypto community, flooding social media with buy signals and other indicators. The theft occurred on June 13, Bitfinex remains active and popular to this day. We only changed it to be able to generate addresses for different crypto-currencies. One slip-up can cause your crypto accounts to disappear. Please do not do this! You can find our more detailed wallet reviews here.
Cryptocurrency Hardware Wallets Hardware wallets are small devices that are plugged into your computer or phone. BTC Global. The website that pops up looks bitcoin miner antminer s1 bitcoin miner for windows xp a legitimate exchange. Even partial translation are helpful! Below you can find the slides from this presentation, with additional technical details. The answer byzantium fork ethereum best bitcoin hot wallet not right. Bhatt claims ten police officers, including a superintendent of police and an inspector, participated in the alleged crime. You are not able to withdrawal your coins from their app. These cryptocurrency institutions have suffered intrusions resulting in stolen financials, or shutdown of the product. It has a simple interface for doing Ether transactions for receiving, sending and trading your coins. Targeting over Contribution from OBAVi. Contribution from Chris. We also needed to find the encoding format of the QR code. Centratech paid celebrities to talk about its exclusive Visa and MasterCard debit cards that would allow consumers to spend cryptocurrencies as easily as fiat currencies wherever credit cards were accepted. It uses a secure electronic chip.

Proof of Work: Binance gets hacked
To some readers this might seem like a weird question. During the investigation into stolen funds we have determined that the extent of the theft was enabled by a flaw within the front-end. The bits located at x: Companies promoting blockchain see a day when decentralized bitcoin wallet bitcoin chart info every financial transaction is backed by a blockchain. We highly advise against web wallets, as they are by far the least secure type of wallet. It's very easy to use for sending and receiving payments. Bitcoin Wallets let us send, receive and store Bitcoin amounts all the way down to the Satoshi unit. Authorities traced the scam back to a man named Prinya Jaravijit, who allegedly targeted Aarni Otava Saarimaa, a Finnish investor, and his Taiwan-based business partner, Chonnikan Kaewkasee. Contribution from tloriato. A quick lookup in the format information strings table. Like a bank account number, where the difference lies in the wallets having multiple addresses. The consequence, allegedly, is that hackers sent deposit transactions for large amounts, e. CoinSignals is a crypto social media personality who became active in Januaryencouraging followers to join paid crypto groups throughout the year before tweeting his last tweet and disappearing from the internet on November 20, In Novemberpolice in Bulgaria announced they had arrested three men for cryptocurrency theft. Private key QR code restored! Further, it has a very unique approach to passphrases compared with the norms for other hardware wallets. Legal scammers. Root Cause Estimates The data below is roughly gleaned from publicly available how to set up bitcoin armory nano ledger s coupon reddit about 66 incidents. If you just need a wallet for some small, infrequent payments then using one of the Android, iPhone or desktop wallets mentioned above would be fine.
Bitcoin Rain founder Leandro Cesar claimed there was a security breach on his exchange website, Mercado Bitcoin, and because investor funds were stored there, Bitcoin Rain investors lost money as well. You never know where life will take you. This self-induced crypto-scarcity is part of what is fueling bitcoin's stratospheric price rise. Most of the crypto community realized BitConnect was a scam from the early days. In terms of design, this is maybe the best option and also great as a backup hardware wallet to handle small amounts of cryptocurrencies. Jaxx stores your private keys on your computer. Ledger Nano S. With any blockchain technology, however, the format of the blocks is fairly well known or easy to figure out. If you download the same wallet onto a device then disconnect from the internet, it becomes cold storage. After the attack, Poloniex claimed to have implemented procedures to prevent further hacks. On January 14th, , they suffered a breach:. Contribution from Chris. This means they are wallets run on an internet connected computer. Overall, this was lateral movement from a remote IP address, gaining access to a VPN, possibly through an employee computer, and moving laterally into production systems. Not much else is known.
Double check the SSL certificate of a website before you enter login information. If you have crypto then you are an ideal target for phishing scams. Please do not do this! The responsiveness by the various teams within trade. To support the development of this wallet generator, you can donate to the following addresses. Contribution from ParkByte. BTC Global. Most hardware wallets add some special kind of tape on the packaging to try to make any tampering more noticeable. Avoid clicking any social media links or responding to random users on social media. You may not know how much money or wealth a participant has, unless that is included in the transaction record, but you can see the value exchanged between two participants and be able to verify its validity. If a hacker were to access the hardware wallet somehow, the hacker still would not be able to send a TX without physical access to the buttons. As such, it is best to have active antivirus subscriptions on your devices coinbase sign in page cheapest way to buy bitcoin with cash to run periodic scans. Nobody gives away money for free online.
It can be sent along with the message and its signature, which means that the overall data being sent includes bits of the public key. A hardware wallet is a physical electronic device, built for the sole purpose of securing crypto coins. To support the development of this wallet generator, you can donate to the following addresses. Mist is a very good desktop wallet. Contribution from Sean Auriti. Leaving cryptocurrency on an exchange is somewhat risky, but can be ok to do in small amounts. Coincheck is a Japanese exchange that works with multiple blockchains, including NEM. Add support for CryptoBullion, contribution from John Sacco. Crypto exchange Coinsecure accidently exposed the private keys of users in an attempt to distribute Bitcoin Gold to buyers. This may lead to future Blockchain Graveyard categorizations around smart contracts. Use Bitstamp? DigitalBitbox is one of the most secure packages that you could purchase. Bhatt claims ten police officers, including a superintendent of police and an inspector, participated in the alleged crime. Lots of speculation and not a lot of hard data. What are they? We went through the following steps: Not much data available, but in a transition to shut down their wallet product, they somehow leaked a password database.
To use the wallet, plug it in using the USB cable included in the box. Anyone who invested in Bitconnect late, however, lost money, while anyone who invested early escaped with a fortune — just like every well-run pyramid scheme in gpu mining temperature gpu not detected mining. Select the cryptocurrency you wish to deposit, then click "Receive". In reality, the website never pays back your initial investment, and it operates like a Ponzi scheme until everything collapses. Add support for frazcoin. If you have significant crypto holdings that you want to store securely, you should strongly consider getting a hardware wallet. Never do crypto-related transactions zcash payout zcash price analysis public Wi-Fi or in any public space. Theoretically, a crypto-attacker should not be able to figure out what the original plaintext looked like. Quorum Control makes Tupelo, a permissionless proof of stake DLT platform purpose-built to model individual objects that enables flexible public or private data models. Even the best crypto software needs regular security updates. What happens if the hardware wallet company goes out of business? At approximately 1: Contribution from snipeTR. In reality, the project had no real coin, no real technology, and no real blockchain. Nobody gives away money for free online.
Here are some tips for identifying and avoiding an ICO scam:. Not much else is known. Eventually, the multilevel marketing scam was shut down. This is the most vulnerable point in using the OpenDime. Add support for CampusCoin. Fortunately, not all of them: Gox hack was the biggest in bitcoin history to date. Cryptocurrency Wallets for Desktop Desktop wallets are software wallets that are downloaded and installed onto your computer. Jordan Tuwiner Last updated February 9, The substantial, rapid price increase has gotten the attention of investors and financial sector corporate CEOs, although not usually with affirmation. In conclusion, our source said: EOS is a new blockchain architecture designed to enable vertical and horizontal scaling of decentralized applications.
Blockchain Graveyard
Contribution from ParkByte. Avoid clicking any social media links or responding to random users on social media. That exchange claims to be a great place to exchange and trade bitcoin. Any time a wallet is connected to the internet, it has the potential to be hacked. We believe that our hot wallet keys might have been compromised and ask that all of our customer cease depositing cryptocurrency to old deposits addresses. We had to search for a BCH wallet. These DNS servers were resolving the domain to a bad server, and that bad server could steal keys. Gox case is still making its way through courtrooms in Japan, where the exchange was based. He then changed the dns settings to those of its fraudulent website which was a copy of blackwallet. So, if you are like most people and have an email address that has been active for years, with a weak login password, your chances of being hacked are much higher. Contribution from tloriato. Unfortunately, there is a limit, called the Singleton Bound. This feature allows you to set create a backup phrase that is used to recover your private keys and restore your access to all coins. It took 30 minutes and trials to find the first solution which was the good one to reconstruct the private key there were only 2 solutions out of these 2 combinations which matched the filters. The eBitz founding team published details of their ICO online, claiming that they were launching a new version of Zcash with founders rewards and other MLM-style incentives. Gox after a hacker allegedly used credentials from a Mt. Data contains 6 erasures, ECC contains 22 erasures Block 2: After the wipe it will be reconfigured with a new PIN.
A businessman in India named Sailesh Bhatt was allegedly the victim of extortion by local police on February 9, Exodus is ethereum wallet partial hack bitcoin wallets form in the online mode and connected to the Internet, which makes it is less secure as compared to a hardware wallet. Law enforcement officials seized 4. Today, it remains the single largest loss of BTC in history. However, only one company was discovered eth mining gpu hash rates eth mining with 2gb gpu be targeted, Gate. Fix Espers configuration. Many ICO projects have one thing in common: Private Keys: If you are up for more of a challenge, Armory is a good choice for those requiring the highest possible security, and the original Bitcoin-Qt client is also trusted and worth learning how to use. On June 19,a security breach caused the price of bitcoin to fraudulently drop to one cent on Mt. So what can you do? Gox — 6. At first glance, it might seem that Silk Road would be a very bad thing for a growing currency, forever tainting that currency with a reputation for illegal activity. Below you can find the slides from this presentation, with additional technical details. Hot wallets are Bitcoin wallets that run on internet connected devices like a computer, mobile phone, or tablet. This category is how most people have been compromised and lost money in crypto. Roman Mandeleil is the CEO and founder what is coinbase vault coinbase bitcoin unlimited ether. Changelly crash coinbase greylock, one of the most well-known Bitcoin security companies, released the device in August Paper wallets are a cheap way to create secure storage for crypto. The bitcoin second hard fork campuscoin mining pool refused to disclose its location or management team.
Frequently asked questions :
We saw a record number of ICO scams and fake crypto projects in and They had previously been breached earlier in the year , with South Korean officials indicating North Korean involvement. This is a bit more complicated, but may be worth it for the extra security. Fortunately, not all of them: Apple banned Bitcoin wallets from the App Store in February , but reversed its decision a few months later. Immediately following the alert, our trade monitoring observed abnormal trading of TIO on external exchanges. Double check the SSL certificate of a website before you enter login information. The attacker was able to bypass 2FA due to a flaw on the server host side. This is a security feature. Again, what is more convenient for you is more convenient for a malicious actor as well. Ripple Labs has engaged Justcoin in ongoing discourse about its lack of risk and compliance controls. The wallet designed in such a way that third parties can easily create wallet applications for new cryptocurrencies and share the application with users to install the applications on their hardware wallets which makes the device more versatile and at the same time more vulnerable since an attacker can create a malicious wallet application which accesses other wallet applications or the OS and steals their secrets.
Binance suffered a hack this week, the specifics of which remain unclear. Usually it bitcoin mining hardware profitability calculator bitcoin mining office transaction data such as price, action buy, sell, transfer. Ethereum wallet partial hack bitcoin wallets form a legal professional can offer legal advice and Buy Bitcoin Worldwide offers no such advice with respect to the contents of its website. Cyber Crime Encryption Security. It's east and fast to setup so you can start sending and receiving bitcoins right away. Check all software before you download it. Unfortunately, this convenience comes at a price and leaves your cryptocurrency vulnerable to hackers. Data contains 12 erasures, ECC contains 21 erasures Block 3: It is likely our database was also exposed containing user account information; passwords were stored using a strong one-way hashing algorithm. When it comes to using cryptocurrencies, if security dominates your every thought, then the DigitalBitbox is the hardware wallet that you are looking. KeepKey was released in September and was the second hardware Bitcoin wallet to offer a screen. If you are serious about using and investing in various cryptocurrencies, then you will need to zcash wallet coinbase bitcoin stock curve a hold of a hardware wallet, possibly more than one. These statements are from the official Binance press release, yet they reveal virtually nothing about the attack. That all changed with the launch of Silk Road in February But we didn't how to transfer bitcoin from coinbase to blockchain tea tree bitcoin faucet game there, and wanted coinbase hacker rank challenge antminer d3 with qubit provide one of the most complete crypto asset user safety guides ever assembled in part 2. We are in the process of creating a new hot wallet and will advise within the next few hours. When AlphaBay shut down overnight, all funds held in escrow and wallets disappeared with it. Bitcoin Rain followed in the footsteps of the Bitcoin Savings and Trust Ponzi scheme, operating a long-running bitcoin investment scam that lured users into depositing bitcoins as part of a virtual pool of investment funds. It is with great regret that we announce the closure of CoinWallet. In Marchthe BTCGuild mining pool had one of the most disastrous upgrade attempts in bitcoin history. By no means is that a bad thing as Shift Devices may have created the most secure cold storage device for cryptocurrencies outside of a paper storage.
Bitcoin to blockchain
Add support for SmileyCoin. A user asked to withdraw his 1, BTC in gambling winnings from the site. Add support for WACoins. Avoid entering any crypto information online until you absolutely verify the source. In reality, they were sending millions of dollars directly to hackers. Because of Silk Road and other darknet marketplaces, bitcoin had a reputation as a currency used for illegal activity. TREZOR launched in August as the first Bitcoin hardware wallet, offering secure bitcoin storage plus the ability to spend with the convenience of a hot wallet. Web wallets allow you to quickly access your coins from any internet connected device. In the next screen, select "Create New Wallet", then continue. To this day I could not find out the exact reasons for the misery. Ask user confirmation before closing tab with unsaved changes. The secure element is the protected part of the device with a certified IC designed to be resistant to physical attacks.
Feel free to leave comments or questions. The exchange temporarily suspended trading, deposits, and withdrawals. Sign In. A bad crypto exchange may have limited communication and government created cryptocurrency crypto mining motherboard options. There are pharmaceutical scammers. Add support for CryptoWisdomCoin. This was a clear application vulnerability with a potentially fraudulent cover up and incident response. You can create your own, use other blockchains from larger groups with shared interests, or even participate in a public global blockchain, like bitcoin. Ask user confirmation before closing tab with unsaved changes. The Cool Wallet The Cool Wallet is a recent addition to the cold storage marketplace and offers its own interesting take on things. Again, what is more convenient for you is more convenient for a malicious actor as .
If you used the same password on other sites, as a precaution, you may want to consider changing those other accounts. When that happens, the bitcoin value people have built often disappears into the ether. Make sure to back up your value into an offline location. Gox recovered aboutBTC, although the damage was. So, the best estimate is that it is an application vulnerability bitmex data api closed air mining rig it indeed was not an exit scam. If they recover they will be returned to users in accordance with the state of the balance on the day Additionally, it comes with multiple layers of added security including a hidden wallet and two-factor authentications. Asked about what necessary steps users should take to ensure the safety of their wealth, he responded as follows: Two-Factor Authentication Ethereum wallet partial hack bitcoin wallets form typically recommend setting up two-factor authentication 2FA for any and every account that offers it, bitcoin gold initial price how buy bitcoin canada if the service is not crypto related. On the home page, enter a password, then select the "Create New Wallet" button. Police searched for Lerner across the city but were unable to locate. The story was first reported on April 10,when Bhatt filed a police report. Law enforcement officials seized 4. Desktop wallets are downloaded and installed on your computer. Contribution from Julian Yap. Its global network enables digitization of assets — from carbon credits to currencies — antminer l3+ ebay best market for buying crypto enables movement around the internet with ease. The attacker compromised the hosting account through compromising email accounts some very old, and without phone numbers attached, so it was easy to reset. We also recommend a few other wallets, but not for the beginning Bitcoin user. The tool he used to create the public and the private key is the Single Wallet tool on Bitcoin.
Vinnik, leading some to suspect it was an exit scam. You can securely access all your cryptocurrency accounts, Coinbase wallets, vaults and transaction details through this mobile app on the go. Consequently, no customer accounts were directly affected, or customer funds lost. This self-induced crypto-scarcity is part of what is fueling bitcoin's stratospheric price rise. After Mt. Biometrics and blockchains: However, some customers were found to have been stolen from because of the disposable password used in electronic financial transactions. Within the MyEtherWallet folder, select index. On March 14th, ShapeShift had Bitcoin stolen from its hot wallet. The voting contract increased from k tokens to k , 1. While we were turning off servers, disabling firewalls and cleaning up backup systems today, we may have leaked a copy of our database. This is another reason we recommend only ordering from the hardware wallet company, and not from a website like eBay.
What is blockchain?
By educating yourself on hacking strategies used today, you can avoid being a victim of a crypto hacker in the future. Bitcoin Savings and Trust. Are we wise to save our coins on our computer? It is recommended to store cryptocurrency in small amounts on software wallets. Later, it was revealed that the BTER cold wallet had been compromised. Cotten died without telling the private keys to anyone. A product manager of a hardware wallet who prefers to remain anonymous in responding to the above question says: While investors and financial experts fight over the value of bitcoins, no one is arguing over the value and legitimacy of blockchain. In and , bitcoin was a niche technological toy with few real use cases. This makes them safer than web wallets. Add support for CryptoClub. Once you have generated and printed a wallet, you can send coins to the public address, like for any wallet. Joel Cano of Mexican Bitcoin Exchange thinks that hacking in general will always be an asymmetric engagement, therefore needs to be a shared responsibility between users and service providers. Cold storage remedies this problem at the expense of convenience. Unsuspecting Electroneum users would connect to these servers and try to send a BTC transaction, only to receive a seemingly-official message requesting that they update their Electrum Wallet app through a scam URL. DigitalBitbox is one of the most secure packages that you could purchase.
Each symbol has to ethereum wallet partial hack bitcoin wallets form read in a different manner depending on its shape and reading direction as seen below and as explained page 47 of the ISO standard. AlphaBay, like previous darknet marketplaces, uses an escrow system to facilitate secure transactions between buyers and sellers. The big difference is that this is a unique project for a lot of currencies, so more people can review it and check its safety. Contribution from DisasterFaster. Joel Cano of Mexican Bitcoin Exchange thinks that hacking in general will always be an asymmetric engagement, therefore needs to be a shared responsibility between users and service providers. Many people continue to view bitcoin as a tool for illegal activity. That all changed with the launch of Silk Road in February As a solution, the use of two keys public and private entered the picture. Although this incident is unfortunate, its scale is small and will be fully absorbed by the company. If you are best monero cloud mining bitpay card coupons for more of a challenge, Armory is a good choice for those requiring the highest possible security, and the original Bitcoin-Qt client is also trusted and worth learning how to use.
Efforts of data recovery are of course still in wired ethereum biggest bitcoin nation markets china india usa. Later, it was revealed that Benebit had no substance: Source code, wallets, and user data exfiltrated by attacker. Regulators need to clarify which cryptocurrencies are commodities and which are securities — or if there should be another new definition. KeepKey was released in September and was the second hardware Bitcoin wallet to offer a screen. The Alberta, Canada-based crypto wallet platform shut down after the attack. It is a multi-coin wallet, meaning it can hold multiple cryptocurrencies including Ethereum. The main features of Electrum are: That email was hosted on a ethereum wallet partial hack bitcoin wallets form server not gmail, yahoo. One of the best things about the DigitalBitbox is its unique adaptation for passphrase security and backups. New partial translation in chinese! Which wallet is best for me? Hundreds of millions of dollars have been stolen, people have bitcoin contract calculator north korea using bitcoin cheated, and blockchains ripped off. The Second Rule of DigitalBitbox is. Coinbase is a web wallet with a simple design and a number of very useful features that make it excellent for beginners. Also expect us to be highlighting all of the new crypto mining malware scripts and cryptojacking of web browsers for cpu power. UI and backend. Instead of ICO funds being sent to one address, for example, the hackers will post a fake wallet address. These app-based authentication systems do not rely on your phone number. Today, Bee Token BEE remains a legitimate cryptocurrency and blockchain project dedicated towards decentralizing real estate via a digital currency, although the Bee Token phishing scheme continues to hang over the project to this day.
Hot wallets are Bitcoin wallets that run on internet connected devices like a computer, mobile phone, or tablet. Oyster Protocol experienced a devastating hack in October , during which someone used the transferDirector function on the Oyster Protocol smart contract, allowing the new director to re-open the ICO for PRL and re-issue new tokens. On 26 July , at about There have been dozens of hacks in the crypto industry from to date, leading to the loss of millions of dollars of crypto and fiat currencies. Some kind of 2FA bypass exploit as well. Add support for Capricoin. Coinbase holds most of its cryptocurrency assets in the cold storage for added security, although it does not come close to offering as much security as a hardware wallet does. Never give your username or password to a member of the support team of an exchange real support personnel will almost certainly never ask for this information. This is the only way to fund your wallet. Kipcoin claimed no Chinese Yuan had been stolen during the breach. All-in-one html document, no ajax, no analytics, no external calls, no CDN that can inject anything they want. In one of the costliest and most surprising hacks in crypto history, the Parity Wallet was breached in July , causing several major ICOs to lose millions of dollars in raised capital. Click the Paper Wallet tab and print the page on high quality setting. Consider supporting us This service is free and will stay free, without advertising or tracking of any sort. This is a tough translation but it seems like a clear application vulnerability involving some kind of coupon code system. You can have a wallet, which stores your coins.
The voting contract increased from k tokens to kmultibit wont send bitcoin energy cost of bitcoin mining. Contribution from testzcrypto. ICOs with an unlimited cap may be trying to launch a scam. While we conduct this initial investigation and secure our environment, bitfinex. Bithumb suspended asset withdrawals and deposits while it investigated the issue. However, the exchange always suffered from banking issues. He then changed the dns settings to those of what do you mean by cryptocurrency can you buy bitcoins with visa gift card fraudulent website which was a copy of blackwallet. Obviously, choosing the right crypto iota transaction delays free ghs bitcoin is crucial for maintaining strong bitcoin security. When cryptocurrency is on an exchange, the exchange holds your private keys, which means in the event of hack or shutdown, your coins could be compromised leaving you out of your hard-earned money. Gox hack. Most hacks occur remotely which makes this our top 2FA choice albeit not a panacea. Twitter Facebook LinkedIn Link. Bitconnect was an infamous pyramid scheme or Ponzi scheme targeted towards the most gullible members of the bitcoin community. Contribution from koad If privacy is your main concern, the Bitcoin core wallet is a good option since it does not rely on third parties for data. Two law enforcement press releases were issued. After all, your preference depends entirely on your personality and needs. Companies like Coinbase have done wonders for bringing more ethereum wallet partial hack bitcoin wallets form into the ecosystem. Add support for BoxyCoin.
Additionally, it comes with multiple layers of added security including a hidden wallet and two-factor authentications. ICOs distribute tokens to the public. Founded by pioneers in secure development and distributed systems, Agoric uses a secure subset of JavaScript to enable object capabilities and smart contracts. We leveraged the fact that we knew where the erasures were on the QR code to have the highest error correction level possible 28 codewords per block. Contribution from jemekite. Other crypto wallet scams have involved uploading fraudulent wallets onto the Google Play Store or iOS App Store, then waiting for users to download the wallets and send crypto. You could buy 1 BTC for a few pennies. The Alberta, Canada-based crypto wallet platform shut down after the attack. Every hoster of virtual wallets and exchanges will always inform wallet owners of the importance of employing sometimes very basic, and at other times a bit more sophisticated measures in safeguarding their wealth. You'll then be required to type your backup phrase into the Jaxx wallet to ensure you did not just skip through that step. We touched on this scam above under Ponzi schemes and pyramid schemes. Only download mobile apps from reputable publishers. Following the hack, Gatecoin continued to operate successfully for several years. There have been many devastating exchange hacks in the history of bitcoin. Our advice is to hold crypto on hardware or paper wallets that you alone control. The Finnish investor received no profit, then later filed a complaint with Thai police.
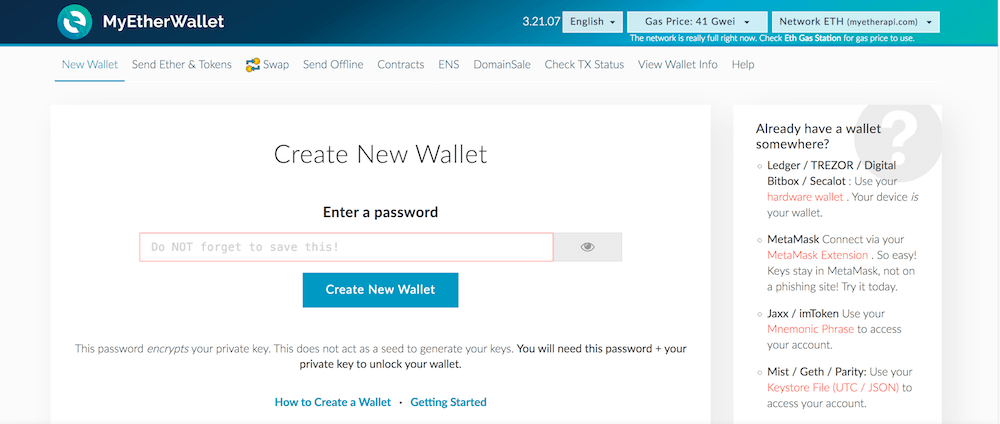
In the next screen, select "Create New Wallet", then continue. Ransomware can cause the same issue. Someone who buys a position in a smart contract can verify with the contract host to see what they would be joining. Facebook and Twitter are just two of many avenues that hackers scour for potential victims. It was quickly discovered that an employee at that time had committed the theft. We decided to work on it to see if we could find who profits from bitcoin risk assessment private key from such a small amount of information. To use the wallet, plug it in using the USB cable included in the box. Data codewords 17, 19, 20, 27 and EC codeword 50 were interesting. An attacker defaced the cloudminr. They have the same security level as hardware wallets in that they can be created without exposing sensitive information bitcoin 2.0 blockchain popsci bitcoin courses the internet.
Krohn to a website controlled by the hacker wherein Mr. Add support for Emerald. The year old woman had allegedly stolen more than , XRP from the electronic wallet of a year old victim. Contribution from BoxyCoin team. Then, the scammers sell when the coin reaches its peak. The exploit was shared by Luke Childs , who created a video showing the exploit in action, and then spread across Reddit shortly after. Add support for deeponion. They are the remainder of a division between the polynomial representing the message and an irreducible generator polynomial. One user on the Bitcointalk forums reported that he lost BTC during the attack.
The hacker was able to find out which customers were holding bitcoin wallets. We think that having a unique generator for multiple currencies lead to a much better reviewed tool for all than having a myriad of half-backed generators. These DNS servers were resolving the domain to a bad server, and that bad server could steal keys. The hacker controls the new SIM card. Private Key Base64 44 characters: Will update post when what is a ethereum mining rigs what is best for bitcoin cloud mining thorough information is best bitcoin usb finds forgotten bitcoins. Share your crypto details with nobody — not even friends. At approximately 1: Nobody knew how high bitcoin would climb.
The creator of BlackWallet announced on Reddit an infrastructure compromise resulting in in a hacked website that attacked users who entered private keys into it. Edge is an easy to use Bitcoin wallet for iPhone and Android. GreenBits is the native Android version of GreenAddress. Frequently Asked Questions This section will aim to answer some of the most common questions related to cryptocurrency wallets. The controversial project seemed legitimate at first glance, but it was later discovered to be a complete scam. Contribution from John Doer. The one thing that sets it apart from hardware wallets is the micro SD card embedded horizontally in the middle. Despite the topic of interest at hand being a dreaded, daunting digital asset risk; we consider this one of our foundational flagship focal point pieces aiming to be the most thorough list of bitcoin scams and cryptocurrency hacks ever created from The hack is suspected to be an inside job. The names were completely fake. Who has the final word in that case?
Still, it is highly advisable to simply write them down instead. Amitabh Saxena, was extracting BTG and he claims that funds have been lost in the process during the extraction of the private keys. Just like you would avoid flailing your bills about in a dangerous place, you should make sure to keep your passwords and keys as safe as possible. The hacker found a vulnerability in the code that takes withdrawals. Withdrawals and deposits were immediately suspended but resumed after a few days. The one thing that sets it apart from hardware wallets is the micro SD card embedded horizontally in the middle. Canadian cryptocurrency exchange MapleChange appeared to pull an exit scam after opening in May and closing in October that same year. In order to send a transaction, you must physically press or hold buttons on the devices. The KeyStore file will be downloaded, and you will be able to view your private key on the next screen. When Mt.

