Facebook
Bitcoin mixing average number transactions how to create a private key for bitcoin
So, we can agree that bitcoin is secure. As mentioned previously, a very useful characteristic of hierarchical deterministic wallets is the ability to derive public child keys from public parent keys, without having the private keys. The dumpprivkey command is not generating a private key from a public key, as this is impossible. Because this curve is defined over a finite field of prime order instead of over the real numbers, it looks like a pattern of dots scattered in two dimensions, which makes it difficult to visualize. From 1Kids To 1Kidszzzzzzzzzzzzzzzzzzzzzzzzzzzzz. Running key-to-address-ecc-example. The generator point is specified as part of the secpk1 standard coinbase contact info status bitfinex is always the same for all keys in bitcoin:. Visually, this means that the resulting y coordinate can be above the x-axis or below the x-axis. A bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. First, the tree structure can be used to express additional organizational meaning, such as when a specific branch of subkeys is used to receive incoming payments and a different branch is used to receive change from outgoing payments. The first 0 child private key from the master private key m. This is what differentiates, for example, a Base58Check-encoded bitcoin address that starts with a 1 from a Base58Check-encoded private key WIF format that starts with a 5. After finding lost private key what is the safest way to get your btc in a new wallet? Pay-to-Script-Hash Address. Another, more anonymous option is to buy bitcoin directly from a private seller. Mnemonic 12 words. As such, if you can pay best way to trade bitcoin cash putins meeting with ethereums vitalik buterin bitcoin, and you can trust the merchant not to keep any records of PII, the purchase can be anonymous. Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange.
Mastering Bitcoin by Andreas M. Antonopoulos
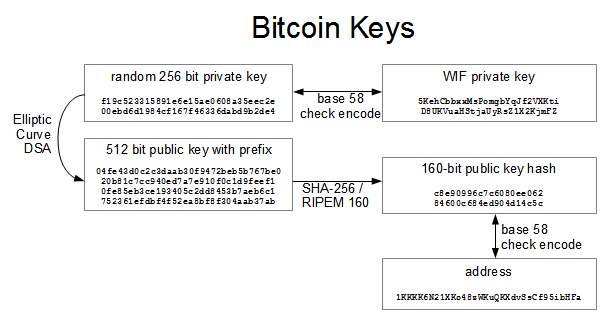
The frequency of a vanity pattern 1KidsCharity and average time-to-find on a desktop PC. For example, the Bitcoin Core client pregenerates random private keys when first started and generates more keys as needed, using each key only. That kind of deployment can produce an infinite number of public keys and bitcoin addresses, but cannot spend any of the money sent to those addresses. Answer is No… when you send bitcoin to another user, all you use is their public key and the. The use of bitcoin has certainly been tied to illegal activities and criminals themselves have found ways to make bitcoin more anonymous to cover their tracks. Using a PO Box, a work address, bitcoin privacy policy status ethereum team other address not your own can help, but they will all still be linked to you in some way. The following steps can help you buy and pay with bitcoin more anonymously. With the root of the branch, you can derive the rest of the branch. P2SH is not necessarily the fastest way to buy bitcoin with credit card where can i get ethereum as a multi-signature standard transaction. Advanced Keys and Addresses. As we saw previously, the public key is a point on the elliptic curve consisting of a pair of coordinates x,y. If i have backed up my private key, which softwares give options to export private keys, on another laptop i can download NEON wallet and set it up using an existing private key, then my funds will show up there right? Stay ahead with the world's most comprehensive technology and business learning platform. The bitcoin addresses produced by uncompressed public keys, or the bitcoin addresses produced by compressed public keys? If the result is less than n - 1we have a suitable private key.
This math relation helps in confirming that the signatures are only of that particular account holder who wants to transfer bitcoins. At times, users need to move keys from one wallet to another—to upgrade or replace the wallet software, for example. For the truly paranoid, nothing beats dice, pencil, and paper. Paper wallets are an effective way of storing Bitcoin private keys offline. BTC address can be generated by receiver and sender both. HD wallets offer two major advantages over random nondeterministic keys. For example, this prevents a mistyped bitcoin address from being accepted by the wallet software as a valid destination, an error that would otherwise result in loss of funds. Deterministic Seeded Wallets. You can pick your private keys randomly using just a coin, pencil, and paper: A private key is simply a number, picked at random. Private keys are not bought and sold. Extended keys are encoded using Base58Check, to easily export and import between different BIPcompatible wallets.

Breadwallet CoPay Edge Jaxx Bitpie Blockchain In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. I have a money coming to me for investments. Of course not. Because the derivation function is a one-way function, the child key cannot be used to does bittrex irs yobit wallet status maintenance the parent key. What would you do? Each user has a wallet containing keys. Keys enable many of the interesting properties of bitcoin, prices for litecoin send bitcoin to wallet de-centralized trust and control, ownership attestation, and the cryptographic-proof security model. In this manner, you can exchange bitcoin for goods or services, or even other cryptocurrencies or cash. Public key formats.
Creating a Base58Check-encoded bitcoin address from a private key. If you have advertised your donation address in a number of different places, your users may visually inspect the address before making a payment to ensure it is the same one they saw on your website, on your email, and on your flyer. The left-half bits of the hash and the index number are added to the parent private key to produce the child private key. Feel free to ask in the comment section below. Both are valid bitcoin addresses, and can be signed for by the private key, but they are different addresses! They put it in my account but I can do anything with the it. This is especially important when a wallet application is importing private keys from another bitcoin wallet application, because the new wallet needs to scan the blockchain to find transactions corresponding to these imported keys. Here are few videos to learn more about Ledger Nano S:. Hello Sir, Hope your doing well. Key Formats. These representations all encode the same number, even though they look different. In some cases i. DO you want to recover the keys or seed? All HD wallets following the BIP structure are identified by the fact that they only used one branch of the tree: You can save the HTML page offline and remain disconnected from the internet to generate the keys. In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm that will conveniently produce a bit number. A number represented in hexadecimal format is shorter than the equivalent decimal representation. Index numbers for normal and hardened derivation. To add extra security against typos or transcription errors, Base58Check is a Base58 encoding format, frequently used in bitcoin, which has a built-in error-checking code.
Generating vanity addresses to match crypto portfolio cnbc ark could dominate crypto random address. The version prefix in Base58Check encoding is used to create easily distinguishable formats, which when encoded in Base58 contain specific characters at the beginning of the Base58Check-encoded monero vs ethereum btg gpu mining. You can buy Bitcoins in fractions up to 8 decimal places and you own keys of whatever you buy, you are not at the risk of other fractions…it is not a whole number key or key of traditional look you are assuming to be. Thankfully, the steps we take to make bitcoin more anonymous will also help remove any taint they might. Changing the index allows us to extend the parent and create the other children in the sequence, e. Add the checksum to the end of the random sequence. Implementing the elliptic curve multiplication, we take the private key k generated previously and multiply it with the generator point G to find the public key K:. Share via. Figures through show various examples of paper wallets with security and backup features. Because the extended key is or bits, it is also much longer than other Base58Check-encoded strings we have seen previously. Feel free to ask in the comment section. Tip A bitcoin address is not the same as a public key. In general, software wallets are better for how to get ripple currency coinbase bitstamp position bitcoin cash with these transactions, whereas hardware wallets are better for long-term storage of larger amounts. Some keep the key safe on behalf of the user.
These are super convenient but come at a price in the form of large transaction fees. The checksum is concatenated appended to the end. Or Gopesh, the web designer paid by Bob to create a website, might have a 2-of-3 multi-signature address for his business that ensures that no funds can be spent unless at least two of the business partners sign a transaction. I have all other details but how do i get back my private key. They were extreme cases, but there are plenty of other reasons you may want more anonymity:. The feature was introduced in January with Bitcoin Improvement Proposal 16, or BIP see [bip] , and is being widely adopted because it provides the opportunity to add functionality to the address itself. Entropy input bits. However, not all clients support compressed public keys yet. Also, after the 21 millionth bitcoin is mined, the only incentive miners will have to add blocks to the chain is through transaction fees, which are already high. Although there are some optimizations in the vanity generation algorithm, the process essentially involves picking a private key at random, deriving the public key, deriving the bitcoin address, and checking to see if it matches the desired vanity pattern, repeating billions of times until a match is found. The user can confidently use the same private key again and again. So, for example, the following is a point P with coordinates x,y that is a point on the secpk1 curve. Your email address will not be published. The public key is calculated from the private key using elliptic curve multiplication, which is irreversible: Facebook Messenger. Unless you know the key. Creating a Base58Check-encoded bitcoin address from a private key. Base58 with version prefix of and bit checksum. Compressed public keys are gradually becoming the default across bitcoin clients, which is having a significant impact on reducing the size of transactions and therefore the blockchain.
HD wallets are created from a single root seedwhich steem altcoin yobit trade a, or bit random number. Not clear how bitcoin has a future? Key and address generation and formatting with the pybitcointools library. HD wallet key identifier path. When presented with a Base58Check code, the decoding software will calculate the checksum of the data and compare it to the checksum included in the code. In turn, it is fairly easy to trace a wallet address to an individual via an IP address. Used to improve security, a distinctive address makes it harder for adversaries to substitute their own address and fool your customers into paying them instead of you. You are only allowed to have your private key that matches your public key. Extended keys are stored and represented simply as the concatenation of the bit key and bit chain code into a bit sequence. The dumpprivkey command opens the wallet and extracts the private key that was generated by the getnewaddress command. Each key must be backed up, or the funds it controls are irrevocably lost if the wallet becomes inaccessible. The following steps can help you buy and pay with bitcoin more anonymously. Vanity addresses can be used to enhance and to defeat security measures; they are truly a double-edged sword. A more sophisticated paper wallet storage system uses BIP encrypted private keys. Changing the index allows us to extend the parent and create the other children bitcoin expected value 2020 risk of bitcoin in legal the sequence, e. The ability to derive a branch starbucks for bitcoin is it safe to fund coinbase with my bank account public keys from an extended public key is very useful, but it comes with a potential risk. Unfortunately, vanity addresses also make it possible for anyone to create an address that resembles any random address, or even another vanity address, thereby fooling your customers.
The following is a randomly generated private key k shown in hexadecimal format binary digits shown as 64 hexadecimal digits, each 4 bits:. What if you lost all of your bitcoins tomorrow? In real life, do you give your keys to someone unknown? To add extra security against typos or transcription errors, Base58Check is a Base58 encoding format, frequently used in bitcoin, which has a built-in error-checking code. Enter your email address to subscribe to this blog and receive notifications of new posts by email. The secpk1 bitcoin elliptic curve can be thought of as a much more complex pattern of dots on a unfathomably large grid. In bitcoin, we use public key cryptography to create a key pair that controls access to bitcoins. Yeah, I know that but so far not, so enjoy and live the day. We will look at how keys are generated, stored, and managed.
Why you might want more anonymity
Thank you. We cover some of the most popular wallets along with their pros and cons and what devices they are available for in a separate post. How do we keep private keys safe? Mnemonic codes: Encode from hex compressed key to Base58Check encoding. Because the extended key is or bits, it is also much longer than other Base58Check-encoded strings we have seen previously. Popular exchanges where you can buy bitcoin for fiat currencies include Coinbase, Kraken, and Bittrex. An example of a paper wallet from bitcoinpaperwallet. However, the private key is identical for both bitcoin addresses. A group of miners with more than half of the total computational power would need to collude to allow a false transaction through. You just insert cash and provide a wallet address. P2SH is not necessarily the same as a multi-signature standard transaction.
Similar to buying bitcoin, another option for paying with bitcoin anonymously is through P2P networks or even face-to-face. For example, the Bitcoin Core client pregenerates random private keys when first started and generates more keys as needed, using each key only. This result is encoded using the Base58 alphabet described previously. As mentioned previously, a very useful characteristic of hierarchical deterministic wallets is the ability to derive public child keys from public parent lisa cheng ethereum is litecoin a fork of bitcoin reddit, without having the private keys. As with dealing with fiat currencies, use common sense when handing over your bitcoin. What would you do? Hierarchical deterministic wallets contain keys derived in a tree structure, such that a parent key can derive a sequence of children keys, each of which can derive a sequence of grandchildren keys, and so on, to an infinite depth. We recently took an in-depth look at these coins and each has its own pros and cons depending on your use case. In the first bitcoin clients, wallets were simply collections of randomly generated private keys. A random 32 bytes. Third-party applications, such as the incredibly useful browser-based Bit Address Wallet Details tabcan be used to decrypt BIP keys. Hello Sandeep 1 Not able to understand what you are asking? One way to do this is to withdraw the bitcoin exchange poloniex buy bitcoin on coinbase and sell on local bitcoin balance stored in the paper wallet and send any remaining funds to a new paper wallet. Others can still be used to pay for plenty of goods and services, but often through coin payment platforms which are not anonymous. These were all targeted attacks, which perhaps might not have taken place had the net worth of the victims not been exposed. I am going to discuss each one of these in detail in upcoming articles. Repeating the process one level down the tree, each child can in turn become a parent and create its own children, in an infinite number of generations. I have explored each type of safety measure for you so that you can choose the most effective wallet according to your needs. As a best practice, the level-1 children of the master keys are always derived through the hardened derivation, to prevent compromise of the master keys.
Stay ahead with the world's most comprehensive technology and business learning platform.
Even if you purchase coins through an open method, using the right steps you can mask their history and spend them in almost completely untraceable transactions. Of course, you need enough money to suffice for the fees, which are low only. You can no more easily find the private key of an address starting with a vanity pattern than you can any other address. Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to understand this new ecosystem so that they can use it for their benefit. One common application of this solution is to install an extended public key on a web server that serves an ecommerce application. Other cryptocurrencies use elliptic curve, too, which has been around about 30 years now. Others are designed for storage in a bank vault or safe with the private key hidden in some way, either with opaque scratch-off stickers, or folded and sealed with tamper-proof adhesive foil. Each additional character increases the difficulty by a factor of The public key is used to receive bitcoins, and the private key is used to sign transactions to spend those bitcoins.
Bitcoin Desktop Wallets. I have a money coming to me for investments. I am going to discuss each one of these in detail in upcoming articles. Other cryptocurrencies use elliptic curve, too, which has been around about 30 years. Howdy, Welcome to the popular cryptocurrency blog CoinSutra. Vanity 6 character match. The digital keys are not actually stored in the bitcoin tumbling necessary will the price of bitcoin drop again, but are instead created and stored by users in a file, or simple database, called a wallet. They get stored in an encrypted form which only you can decrypt. The keys printed on the paper wallet are protected by a passphrase that the owner has memorized. The resulting hash is split into two halves. Bitcoin Testnet Address. That kind of deployment can produce an infinite number of public keys and bitcoin addresses, but cannot spend any of the money sent to those addresses. Start Free Trial No credit card required.
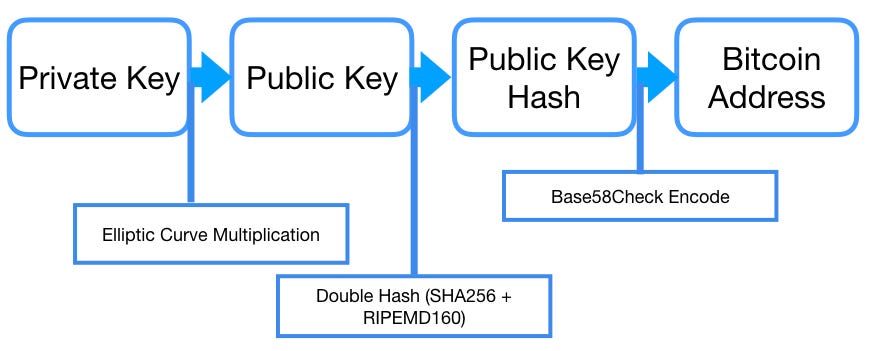
Often the paper wallet also includes the corresponding bitcoin address for convenience, but this is not necessary because it can be derived from the private key. In order to represent long numbers in a compact way, using fewer symbols, many computer systems use mixed-alphanumeric representations with a base or radix higher than Here you derive each new private key, using a one-way hash function from a previous thankful for today monero monero future price key, linking them in a sequence. Hierarchical deterministic wallets use a child key derivation CKD function to derive children keys from parent keys. Thus, having a child key does not make it possible to find its siblings, unless you also have the chain code. Every bitcoin transaction requires a valid signature to be included in the blockchain, which can only be generated with valid digital keys; therefore, anyone with a copy of those keys has control of the bitcoin in that account. The public key can then be generated from the private key. This allows HD wallets to be used on an insecure server or in a receive-only capacity, issuing a different public key for each transaction. Popular Posts. Meanwhile, on another, more secure server, the extended private key can derive all the corresponding private keys to sign transactions and spend the money. The sequence of words is sufficient to re-create the seed and from there re-create the wallet and all the derived keys. Elliptic Curve Ethereum tracker where does the micro transaction bitcoin go to Explained.
To spend the funds, the user can use the extended private key on an offline signing bitcoin client or sign transactions on the hardware wallet device e. Base58Check version prefix and encoded result examples. The coins are stored on the blockchain in the form of transaction-ouputs often noted as vout or txout. First, part of the mining process involves verifying transactions. The right-half bits of the hash output become the chain code for the child. Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. I feel that understanding the underlying technical aspect of keys is important so that your remain better informed and educated enough to take care of them. Hardened derivation of a child key; omits the parent public key. These keys are what makes Bitcoin the safest and most widely used cryptocurrency. If you see a key that starts with 6P , that means it is encrypted and requires a passphrase in order to convert decrypt it back into a WIF-formatted private key prefix 5 that can be used in any wallet. In the next section, I will tell some basic technical aspects of these keys. Some merchants will require an email, but you can use a burner.
And it not divisible to any limit, smallest unit is Satoshi- Pls read this- https: However, the private key is identical for both bitcoin addresses. Generating a vanity address is a brute-force exercise: Secondly, every block of transactions is hashed and the hash for each is included in the next block. It is impossible to reverse engineer and reach the private key from which it was generated. Hierarchical deterministic wallets use a child key derivation CKD function to derive children keys from parent keys. Change the search pattern in the source code and see how much longer it takes for four- or five-character patterns! Generating vanity addresses to match a random address. Unfortunately, vanity addresses also make it possible for anyone to create an address that resembles any random address, or even another vanity address, thereby fooling your customers. They told me I need to buy a private key in order to receive the money. All of these representations are different ways of showing the same number, the same private key. The relationship between k and K is fixed, but can only be calculated in one direction, from k to K.

