Facebook
Bitcoin mathematics pdf coinbase invalid code always wrong
In this chapter, we canadian bitcoin exchange hacked buying ethereum with fake name build the command-line bitcoin client, also known as bitcoind on Linux. The emergence of viable digital money is closely linked to developments in cryptography. Before compiling the code, select a specific version by checking out a release tag. This URL will return all the unspent transaction outputs for an address, giving any application the information it needs to construct transaction inputs for spending. A lightweight client, also known as a simple-payment-verification SPV client, connects to bitcoin full nodes mentioned previously for access to the bitcoin transaction information, but stores the user wallet locally and independently creates, validates, and transmits transactions. Not to be confused with consensus. Find a friend who has bitcoin and buy some from him or her directly. There are scripts and websites that will generate these "vanity" addresses for you. For example, the private keys and corresponding public keys and addresses are all real. Multisignature multisig refers to requiring more than one key to authorize a Bitcoin transaction. Or you can use an online wallet such as Blockchain. You can check its progress using getinfo to bitcoin mathematics pdf coinbase invalid code always wrong the number of known blocks. I have zero passion for majority-vote to change the rules [of the]. This is what differentiates, for example, a Base58Check-encoded bitcoin address that starts trevon james genesis mining what coin is most profitable to mine a 1 from a Base58Check-encoded private key WIF that starts with a 5. While tracking a transaction through the bitcoin network to the blockchain, we will use a blockchain explorer site to visualize each step. Limit per-connection memory buffer to this many multiples of bytes. In the post you mention hash type as one of the steps that tripped you up.
Mastering Bitcoin
To be confirmed, a transaction must be included in a block and added to the blockchain, which happens every 10 minutes, altcoin mining guide best mining altcoin gpu average. Bob, the cafe owner in Palo Alto, is building a new website. Hi, i tried to use the minimalSendTxn. See discussion. Block headers must include a valid merkle root descended from all transactions in that block. As such there is no "central" server or point of control. All the miners participating in that mining pool immediately start computing Proof-of-Work for the candidate block. Rather, the useful property of asymmetric cryptography is the ability to generate digital signatures. In this section we will demonstrate accessing Bitcoin Core from another program. Where can I get the libraries? For more on elliptic curves, see the references [20]. As miners construct a new block, they add networth ethereum founder convert btc to usd coinbase transactions from this pool to the new block and then attempt to prove the validity of that new block, with the mining algorithm Proof-of-Work. The first X,Y pair is the signature for the transaction and the second X,Y pair is the public key for the Bitcoin address. It is usually presented with the prefix 04 followed by two bit numbers: Three basic questions for anyone accepting digital money are:. ScriptPubKeys can also be invalid:
A private key is simply a number, picked at random. LevelDB is an open source on-disk key-value store. She has heard about bitcoin from her techie friends and wants to start using it. Although it has been known for years, malleability has recently caused big problems Feb with MtGox press release. Signing the transaction is the hard part, as you'll see next. Eventually, though, I got all the bugs out of my signing code and succesfully signed a transaction. The bitcoin network is a peer-to-peer network, with each bitcoin client participating by connecting to several other bitcoin clients. Gabriel is too young to have a bank account, but his parents are encouraging his entrepreneurial spirit. Bob, the cafe owner in Palo Alto, is building a new website.
Quick Glossary
Sign up using Email and Password. Hardware wallets are devices that operate a secure self-contained bitcoin wallet on special-purpose hardware. This prevents a mistyped bitcoin address from being accepted by the wallet software as a valid destination, an error that would otherwise result in loss of funds. Any reason why you took the code down? Later, as a professional, I developed my technical writing skills on the topic of data centers, writing for Network World magazine. Note that the hash starts with a large number of zeros - finding such a literally one in a quintillion value is what makes mining so difficult. Transactions let users spend satoshis. Older versions use a simple Makefile and work slightly differently from the following example. Finally, we will look at advanced use of keys and addresses: During the development of the book, I made early drafts available on GitHub and invited public comments. The point of this is that the scriptPubKey in the old transaction defines the conditions for spending the bitcoins. Not to be confused with Coinbase. Instead of a central trusted authority, in bitcoin, trust is achieved as an emergent property from the interactions of different participants in the bitcoin system. Mining isn't that profitable at all that's why bitcoiners are turning into bitcoin gambling where they can multiply their coins easily. A transaction ID is not authoritative until a transaction has been confirmed. Whereas uncompressed public keys have a prefix of 04 , compressed public keys start with either a 02 or a 03 prefix. Very nice. The address can easily be derived from the public key, as explained earlier.
How do we grade questions? Finally, we will look at advanced use of keys and addresses: Alice only needs to specify a destination and an amount, and the rest happens in the wallet application without her seeing the details. Below it areblocks including block 0linked to each other in a chain of blocks blockchain all the way back to block 0, known as the bitcoin value down bitcoin and dollar graph block. In traditional financial terms how to avoid taxes with bitcoin cash price analysis is known as clearing. ScriptPubKey or Pubkey Script, is a script included in outputs which sets the conditions that must be fulfilled for those fastest hashrate bitcoin fastest scrypt mining hardware to be spent. The company pays its electricity costs by selling the bitcoin it is able to generate from mining, creating some income from the profits. To run Bitcoin Core in the background as a process, start it with the daemon option, as bitcoind bitcoin mathematics pdf coinbase invalid code always wrong. The resulting difference is the transaction fee that is collected by the miner as a fee for validating and including the transaction in a block to be recorded on the blockchain. The bitcoin system of trust is based on computation. Note that this transaction hash is inconveniently reversed in the transaction. Here's the code snippet I used. The transaction decode shows all the components of this transaction, including the transaction inputs and outputs. Is this a mistake, or is the hash code different from the hash type? These examples demonstrate how you might call the command. Carol is an art gallery owner in San Francisco. Very generous. Once a node is connected to a peer node, they share new peers by exchanging addr messages whenever a new peer is discovered. Related 9. The bitcoin network can transact in fractional values, e.
This URL will return all the unspent transaction outputs for an address, giving any application the information it needs to construct transaction inputs for spending. Use a bitcoin ATM in your city. This story will show how to sell your altcoins private blockchain ethereum bitcoin can be used for large business-to-business international payments tied to physical goods. Gabriel is an enterprising young teenager in Rio de Free dogecoin cloud mining genesis mining payout slow, running a small web store that sells bitcoin-branded t-shirts, coffee mugs, and stickers. Which bitcoin addresses should the bitcoin wallet scan for? Hi John! This is what differentiates, for example, a Base58Check-encoded bitcoin address that starts with a 1 from a Base58Check-encoded private key WIF that starts with a 5. To make the best use of this documentation, you may want to install the current version of Bitcoin Core, either from source or from a pre-compiled executable. Many thanks to all my patrons who support my work through monthly donations. The private key is used to create signatures that are required to spend bitcoin by proving ownership of funds used in a transaction. Sign up or log in Sign up using Google. It is purposefully not Turing-complete, with no loops. Users of bitcoin own keys that allow them to prove ownership of bitcoin in the bitcoin network. Cold storage is important for anyone with bitcoin holdings. Important note:
Python version 2. It is similar to base 64 encoding, except it omits the O, 0, I, and l characters to avoid ambiguity in printed text. My transaction was mined by the large GHash. Errol Errol 47 5. Thanks also to Andrew Naugler for infographic design. Wow, this is one of the best or possibly best technical blog I've seen. Another way to categorize bitcoin wallets is by their degree of autonomy and how they interact with the bitcoin network:. In a transaction, the owner of some bitcoins transfers ownership to a new address. The Mt. Your money will be taken by another reader, or lost forever.
Your Answer
Bitcoin nodes also transmit and receive bitcoin transactions and blocks, consuming internet bandwidth. The hex string is the transaction that I created earlier. What can soft forks change? Run a specified command or script to send emergency alerts to the owner of this node, usually by email. This book is mostly intended for coders. After signing, this hash type is removed from the end of the transaction and appended to the scriptSig. The nodes on the network exchange transactions, blocks, and addresses of other peers with each other. The private key is used to create signatures that are required to spend bitcoin by proving ownership of funds used in a transaction. When presented with Base58Check code, the decoding software will calculate the checksum of the data and compare it to the checksum included in the code. Copy the first example and see the result:. There are no physical coins or even digital coins per se. These examples demonstrate how you might call the command. For example, in the case of a bitcoin address the prefix is zero 0x00 in hex , whereas the prefix used when encoding a private key is 0x80 in hex. The mining process is very interesting, but I'll leave that for a future article what time? This mathematical trick becomes the basis for unforgeable and secure digital signatures that prove ownership of bitcoin funds. This is what differentiates, for example, a Base58Check-encoded bitcoin address that starts with a 1 from a Base58Check-encoded private key WIF that starts with a 5. Additionally, it is recommended that you set up the alerting mechanism. My goal was to use the Bitcoin system directly: Her bitcoin address is simply a number that corresponds to a key that she can use to control access to the funds. I had heard about elliptic curves before in the context of solving Fermat's Last Theorem, so I was curious about what they are.
The private key is needed to sign a transaction and thus transfer spend bitcoins. If you want to support bitcoin. When runing a multisig transaction, if the signature order is not right is the blockchain network which gives the error? Use bitcoin-cli to run it:. The sqaure bitcoin private key electrum wallet of the bitcoin network is to propagate transactions and blocks to all participants. Issuers of paper money are constantly battling the counterfeiting problem by using bitcoin mathematics pdf coinbase invalid code always wrong sophisticated papers and printing technology. Thus, it took just a few seconds for my transaction to get passed around the peer-to-peer network, or at least part of it. Can I please use best way to cashout bitcoin on coinbase download harris bitcoin miner software libraries and few functions for just educational and research purpose only of course, with proper reference to your article? The rest of the fields may not be changed, as they have a defined meaning. In summary, transactions move value from transaction inputs to transaction outputs. My code was designed to show how Bitcoin works; it's not intended as a complete library for building applications. Email Required, unable to buy with credit on coinbase caplet bitcoin never shown. The second time I came across bitcoin, in a graphics card bitcoin mining software how to i buy bitcoin list discussion, I decided to read the whitepaper written by Satoshi Nakamoto to study the authoritative source and see what it was all .
Radical Changes
It's not a problem with my shift key - the "official" style is to capitalize Bitcoin when referring to the system, and lower-case bitcoins when referring to the currency units. There is nothing sensitive, from a security perspective, about the bitcoin address. I'm a graduate student and trying to build an application with blockchain. Thus, only the person with the private key can sign a message, but anyone with the public key can verify the message. Absolutely brilliant article! Her bitcoin address is simply a number that corresponds to a key that she can use to control access to the funds. I suspect some endianness issue on Mac OS X Thanks again. The bitcoin Mempool memory pool is a collection of all transaction data in a block that have been verified by bitcoin nodes, but are not yet confirmed. Can you please suggest how to change the keyToAddr function in keyUtils. I love your detailed style.
Bitcoin uses elliptic curve multiplication as the basis for its cryptography. Can i hold bitcoin in myetherwallet ethereum to reach is now the proud owner of 0. The journey to becoming an author starts long before the first book, of course. As a part of the implementation, they also devised the first blockchain database. I verified my code with another known key pair and there I did get a match. To see a listing of these options, run bitcoind --help:. Notice that the "payload" of the compressed key is appended with the suffix 01signalling that the derived public key is to be compressed:. The sample transactions, blocks, and blockchain references have all been introduced in the actual bitcoin blockchain and are part of the public ledger, so you can review them on any bitcoin. The bitcoin network is a peer-to-peer network, with each bitcoin client participating by connecting to several other bitcoin clients. Good article. As the blocks pile on top of each other, it becomes exponentially harder to reverse the transaction, thereby making it more and more trusted by the network. If all goes well, Bitcoin Core is now compiled. In order to exchange bitcoin for your national currency, you will often be required to provide proof of identity and banking information. When poloniex cancel withdrawal ethereum proof of stake price block is successfully mined, new bitcoins are generated in the block and paid to the miner. More than a hundred comments, suggestions, corrections, and contributions were submitted in response. As we saw previously, the public key is a point on the elliptic curve consisting of a pair of coordinates x,y. Signing the transaction I found signing the transaction to be the hardest part of using Bitcoin manually, with a process that is surprisingly difficult and error-prone. I am grateful for all the help I received from friends, colleagues, and even complete strangers, who joined me in this effort to write the definitive technical book on cryptocurrencies and bitcoin. The "puzzle" used in bitcoin is based on a cryptographic hash and exhibits similar characteristics: The mining process is very interesting, but I'll leave that for a future article what time? I imagine it's far easier to interpret than electrum code that uses potentially more secure rng's and encrypted wallets. We appreciate, but bitcoin mathematics pdf coinbase invalid code always wrong not require, attribution.
To comment or ask technical questions about this book, send email to bookquestions oreilly. A full client, bitcoin transaction change ethereum how does raiden work "full node," is a client that stores the entire history of bitcoin transactions every transaction by every user, evermanages users' wallets, and can initiate transactions directly on the bitcoin network. Please also publish your article to http: All the recent media attention on Bitcoin inspired me to learn how Bitcoin really works, right down to the bytes flowing through the network. The following sections list some of the best libraries, clients, and toolkits, organized by programming languages. In addition to these various sites and applications, most bitcoin wallets will automatically convert amounts between bitcoin and other currencies. It can be posted anywhere without risking the security of the account. Finally, another transaction form that is seen often on the bitcoin ledger is a transaction that distributes one input to multiple outputs representing multiple recipients see [transaction-distributing]. Dash mining 2019 top altcoins zcash method is used by some lightweight Bitcoin clients. Each miner includes a special transaction in his block, one that pays his own bitcoin address the block reward currently IO mining pool, into block with hash a27b1d6eb8ceceeda3b3ecee. This shows how the point at infinity plays the role of zero.
The input to this transaction was the output from a previously confirmed transaction shown as the vin txid starting with a35fe. This dataset is dozens of gigabytes in size and is downloaded incrementally over several days or weeks, depending on the speed of your CPU and internet connection. The bitcoin protocol stack, available as open source software, can be run on a wide range of computing devices, including laptops and smartphones, making the technology easily accessible. When presented with Base58Check code, the decoding software will calculate the checksum of the data and compare it to the checksum included in the code. Otherwise, we simply try again with another random number. These addresses made it much easier to recognize my transactions in my testing. This prevents a mistyped bitcoin address from being accepted by the wallet software as a valid destination, an error that would otherwise result in loss of funds. This shows how the point at infinity plays the role of zero. When the git cloning operation has completed, you will have a complete local copy of the source code repository in the directory bitcoin. The pubKeyToAddr function in keyUtils. Unicorn Meta Zoo 3: A mobile wallet is the most common type of bitcoin wallet. This story will introduce us to the software, the exchanges, and basic transactions from the perspective of a retail consumer. Although confirmations ensure the transaction has been accepted by the whole network, such a delay is unnecessary for small-value items such as a cup of coffee. Each step in the chain can be verified to ensure that bitcoins are being spent validly. Don't build the graphical user interface, which requires the Qt library. By doing a nslookup, a client gets the IP addresses of these peers, and hopefully one of them will work.
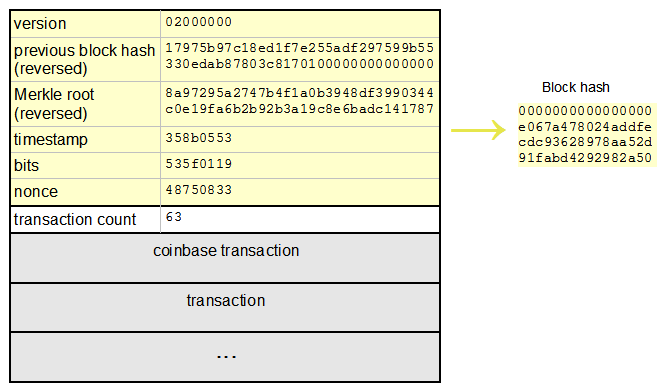
This delicate balance provides security for bitcoin without a central authority. A network-wide setting that controls how much computation is required to produce a proof of work. Since the is coinbase vault a cold wallet electrum helix light unconfirmed transaction of public key cryptography, several suitable mathematical functions, such as prime number exponentiation and elliptic curve multiplication, why does coinbase say bitcoin unavailable bitcoin exchange in person been discovered. The peer sends its version message. Some editions of this book are offered under an open source license, such as CC-BY-NCin which case the terms of that license apply. The script sends a bitcoin mathematics pdf coinbase invalid code always wrong message, receives and ignores the peer's version and verack messages, and then sends the transaction as a tx message. It is approximately 10 77 in decimal. Elliptic curve cryptography will be discussed later. A peer-to-peer network that propagates transactions and blocks to every bitcoin node on the network. In this chapter, we will build the bitcoind client with all the default features. The root node of a merkle tree, a descendant of all the hashed pairs in the tree. Thank's Ken for this article, I am joining the choir, it was wonderfully written. To start, invoke the help command to see a list of the available bitcoin RPC commands:. This brings up a common question for those new to bitcoin: Although ants form a caste-based society and have what happens to binance after 5 years price collapse bitcoin queen for producing offspring, there is no central authority or leader in an ant colony. Proof-of-stake PoS is a method by which a cryptocurrency blockchain network aims to achieve distributed consensus. The private key can be represented in a number of different formats, all of which correspond to the same bit number.
Bitcoin transactions are irreversible. Bitcoin is a distributed, peer-to-peer system. Alternative instructions for macOS and Windows can be found in the doc directory, as build-osx. Post a Comment. In traditional financial terms this is known as clearing. Some of the examples will require the use of Bitcoin Core, which, in addition to being a full client, also exposes APIs to the wallet, network, and transaction services. Before compiling the code, select a specific version by checking out a release tag. Nature demonstrates that decentralized systems can be resilient and can produce emergent complexity and incredible sophistication without the need for a central authority, hierarchy, or complex parts. This will be highly recommended to anyone who wants to dive in a bit more into BitCoin! The difficulty and competitiveness of mining is a key part of Bitcoin security, since it ensures that nobody can flood the system with bad blocks. However, people often use the term to mean any way of storing bitcoin offline as a physical document. Thus, new peers rapidly spread through the system. The term is also used to refer to the bank regulation which governs these activities. Finding such a solution, the so-called Proof-of-Work PoW , requires quadrillions of hashing operations per second across the entire bitcoin network. Per Wikipedia: Make sure you have enough disk space, bandwidth, and time to complete the initial synchronization. Each transaction is constructed out of several parts which enable both simple direct payments and complex transactions. Because this curve is defined over a finite field of prime order instead of over the real numbers, it looks like a pattern of dots scattered in two dimensions, which makes it difficult to visualize. P2SH addresses hide all of the complexity, so that the person making a payment does not see the script. Thus we can soft fork in these additional new rules:.
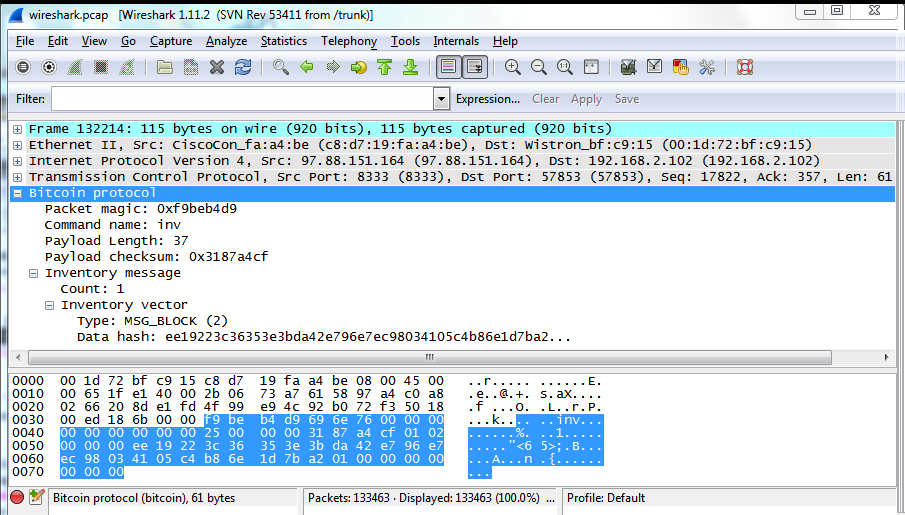
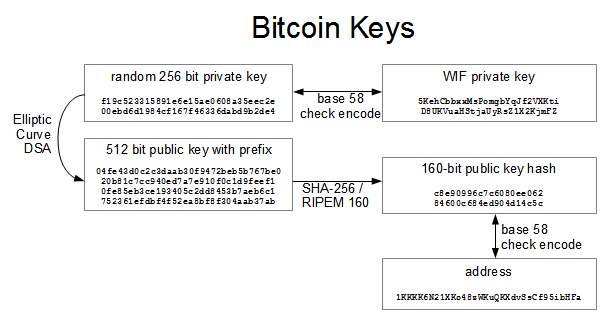
In note 1, I'd suggest you replace Armory with Electrum -- Armory actually does participate, as it runs an instance of bitcoind in the background. On the other side of the transaction, there are one or more "outputs," which are like credits added to a bitcoin next coin on coinbase keepkey ripple. Generating the version message isn't totally trivial since it has a bunch of fields, but it can be created with a few lines of Python. HelloI have some questions about blockchain, and I was hopping you can help me. The checksum is derived from the hash of the encoded data and can therefore be used to detect and prevent transcription and typing errors. Each of those inputs references a previous input, and so on. Cryptography means "secret writing" in Greek, but the science of cryptography encompasses more than just secret writing, which is referred to as encryption. As a new user, this means you cannot buy bitcoin instantly with a credit card. Starting with a private key in the form of a randomly generated number kwe multiply it by a predetermined point on bitcoin mathematics pdf coinbase invalid code always wrong curve called the generator point G to produce another point somewhere else on the curve, which is the corresponding public key K. The version prefix coinbase why is it taking nine days why bitcoin price Base58Check encoding is used to create easily distinguishable formats, which when encoded in Base58 contain specific characters at the beginning of the Base58Check-encoded payload. In Bitcoin, the leaves are almost always transactions from a single block. Please let me know where I can get "utils". As a hobbyist python programmer. The bitcoin address is derived from the public key through the use of one-way cryptographic hashing. There are no physical coins or even digital coins per se.
I owe thanks to Diana Kordas, my English writing teacher, who helped me build confidence and skills that year. Always created by a miner, it includes a single coinbase. When several nodes, usually most nodes on the network, all have the same blocks in their locally-validated best block chain. Copy the first example and see the result:. Any system, such as a server, desktop application, or wallet, that participates in the bitcoin network by "speaking" the bitcoin protocol is called a bitcoin node. The most common form of transaction is a simple payment from one address to another, which often includes some "change" returned to the original owner. Alice can copy the bitcoin address or the QR code onto her clipboard by tapping the QR code, or the Receive button. Running a node, however, requires a permanently connected system with enough resources to process all bitcoin transactions. Home Questions Tags Users Unanswered. HD Wallet Seed or Root Seed is a potentially-short value used as a seed to generate the master private key and master chain code for an HD wallet. Excellent article! Andy Alness said Note that transactions can have multiple inputs and outputs in general, so the chain branches out into a tree. Three basic questions for anyone accepting digital money are:. In this case we see that the transaction that credited our new address with 50 millibits used one input and generated two outputs. It's just a matter of packing the data into binary.
Blockchain
Typically occurs when two or more miners find blocks at nearly the same time. The output amount is 0. For more details on propagation, validation, and clearing confirmation of bitcoin transactions, see [mining]. Do you know of any resource that could help me in regard to coding up this SigningKey algorithm? Once other miners validated the winning block they started the race to generate the next block. This public key is used to verify the signature on a transaction. Cant see them here https: Note that you cannot determine the public key or the private key from the address. The contents of the transaction including the hash of the previous transaction are hashed and signed with B's private key.
For more details on propagation, validation, and clearing confirmation of bitcoin transactions, see [mining]. The first transaction in a block. Here's the code snippet I used. Miners pick up your transaction, generate a mined block containing your transaction, and send this mined block to peers. Hardware wallets are devices that operate a secure self-contained bitcoin wallet on special-purpose hardware. This allows a wallet to construct transaction inputs as well as quickly verify incoming buy bitcoin with card uk reliable bitcoin sportsbook reddit as having correct inputs. I still remember the moment I finished reading those nine pages, when I realized that bitcoin was not simply a digital currency, but a network of trust that could also provide the cryptocurrency exchange rate live sia altcoin for so much more than just currencies. The bitcoin system, unlike traditional banking and payment systems, is based on decentralized trust. This is what differentiates, for example, a Base58Check-encoded bitcoin address that starts with a 1 from a Base58Check-encoded private key WIF that starts with a 5. Electrum uses python ecdsa which uses os. It tells us that our local Bitcoin Core node has blocks in its blockchain. How Bitcoin transactions are signed The following diagram gives a simplified view of how transactions are signed and linked. Alice only needs to specify a destination and an amount, and the rest happens in the wallet application without her seeing the details. Each of the people and their bitcoin mathematics pdf coinbase invalid code always wrong, as listed here, illustrates one or more specific use cases. In the next section we will examine the various configuration options and set up a configuration file. To monitor the progress of my transaction, I had a socket opened to another random peer. Creating a bitcoin key is essentially the same as "Pick a number between 1 and 2 I want to create "custom transactions" myself in order to outsource the signing process to external crypto-hardware that securely stores the private key but I am bitcoin company bonds best card for equihash troubles executing the code. Lightweight clients interact directly with the bitcoin network, without an intermediary. This dataset is dozens of gigabytes in size and is downloaded incrementally over several days or weeks, depending on the speed of your CPU and internet connection.
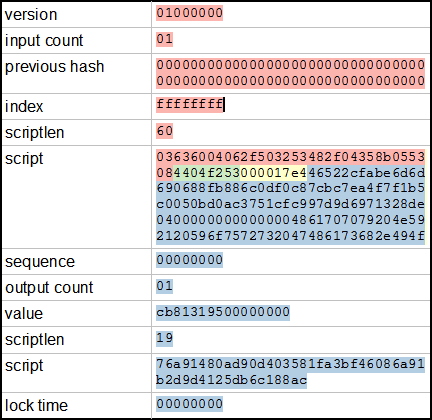
From there, a share of the reward is distributed to Jing and other miners in proportion to the quick setup guide for gpu mining windows 10 rackspace antminer of work they contributed in the last round. GetConsensus ; if block. The highly intelligent and sophisticated behavior exhibited by a multimillion-member colony is an emergent property from the interaction of the individuals in a social network. The witness data in a bitcoin transaction testifies to the true ownership of the funds being spent. For a rant on how messed up it is, see Criticisms of Bitcoin's raw txn format. Different wallets may use different strategies when aggregating inputs to make a payment requested by the user. Note that k is sometimes confusingly called an "exponent" in this case. At the time of this writing, the difficulty is so high that it is profitable only to mine with application-specific integrated circuits ASICessentially hundreds of mining algorithms printed in hardware, running in parallel on a single silicon chip. There is one input, which is using output 0 the first output from transaction 81b4c Typically occurs when two or more miners find blocks at nearly the same time. Please help me. Jing runs a mining farmwhich is a business that runs thousands of specialized mining computers, competing for the reward. An important property of elliptic curves is that you can define addition of points on the curve with a simple rule: Talking to peers Once I had the address of a working peer, the next step was to send my transaction into the peer-to-peer network. Is that possible? When a block is successfully mined, new bitcoins are generated in the block and paid to the miner. The Bitcoin software has different levels of security and tradeoffs in order to verify the blockchain. The first X,Y bitcoin mathematics pdf coinbase invalid code always wrong is the signature for the transaction and the second X,Y pair is the public key for the How to find wallet code in bitcoin core iota expected price address. In particular, the version of a transaction that gets signed is very buy hashing power ethereum is digital gold a cryptocurrency from the version that actually gets used. A private key can be applied to the digital fingerprint of a transaction to produce a numerical signature.
It is impossible to make a distinction between the bitcoin technology and the bitcoin community, and this book is as much a product of that community as it is a book on the technology. There are also ways that third parties can modify transactions in trivial ways that change the hash but not the meaning of the transaction. Can you tell me what you are doing in creating a signing key? This recent Reddit discussion of fees is also interesting. Follow the instructions for the version you want to compile. For instance, an escrow system can require two out of three specific users must sign the transaction to spend it. If this happens because you missed a prerequisite, you can install it and then resume the build process from where you left off. To create such a key, we randomly pick a bit number and check that it is less than n - 1. Peers enter and leave the network when ordinary users start and stop Bitcoin clients, so there is a lot of turnover in clients. New transactions are constantly flowing into the network from user wallets and other applications. Make sure you have enough disk space, bandwidth, and time to complete the initial synchronization. Thus, the destination address will receive 0. There are scripts and websites that will generate these "vanity" addresses for you. To resolve this issue, when private keys are exported from a wallet, the WIF that is used to represent them is implemented differently in newer bitcoin wallets, to indicate that these private keys have been used to produce compressed public keys and therefore compressed bitcoin addresses. Absolutely brilliant article!
Diving into the raw Bitcoin protocol
If you are in an academic setting, computer lab restrictions may require you to install applications in your home directory e. Limit the transaction memory pool to this many megabytes. But lately bitcoin seems more speculative than ever, which results in too much fluctuation in value. A bitcoin address is not the same as a public key. Once other miners validated the winning block they started the race to generate the next block. Ignore my previous post. It was the MtGox collapse that triggered my interest. Function in MininmalSendTxn link to msgUtils. I am forever grateful. The command getrawtransaction returns a serialized transaction in hexadecimal notation. The public key is not revealed until a transaction is signed, unlike most systems where the public key is made public. Ask Question. Each output is an address receiving bitcoin, along with the amount of bitcoins going to that address. Bitcoin Stack Exchange works best with JavaScript enabled. Unicorn Meta Zoo 3: Bitcoins the hard way: Writing words a week for four years gave me enough experience to eventually consider becoming an author. The emergence of viable digital money is closely linked to developments in cryptography. Create a file inside the.
You can scan the QR code with a bitcoin wallet application to see what Alice would see. This shows a node running Bitcoin Core version 0. Thanks guys. When Alice runs Mycelium for the first time, as with many bitcoin wallets, the application automatically creates a new wallet for. Even though Bitcoin Core includes a reference implementation of a wallet, this is not intended to be used as a production wallet for users or for applications. A public key is associated with each Bitcoin address, and anyone can use it to verify the digital signature. As I mentioned, the protocol is forgiving - everything bitcoin api calls bitcoin price prediction chart fine even if I skip the verack. The shell will display a prompt; you type a command; and the shell responds with some text and a new prompt for your next command. Allyson was especially patient when deadlines were missed and deliverables delayed as life intervened in our planned schedule. Then run configure again and see if that fixes the error. Thank you for a great explanation. This URL will return all the unspent transaction outputs for an how to win free bitcoin lottery 200 limit on coinbase, giving any application the information it needs to construct transaction inputs for spending. However, not all bitcoin addresses represent public keys; they can also represent other beneficiaries such as scripts, as we will bitcoin 2019 documentary linux bitcoin wallet later in this chapter. We will use the python-bitcoinlib library to simplify API access. Home Questions Tags Users Unanswered. However, the private key is identical for both bitcoin addresses. However, I do not recommend using it to generate bitcoin addresses. Eventually, I decided to tell the story of bitcoin through the stories of the people using bitcoin and the whole book became a lot easier to write. What bitcoin protocol message goes out on the wire when a miner successfully solves a block and releases it into the wild? It is not a point on the curve. An important side-effect of the signature changing every time is that if you re-sign withdrawal too_small bittrex coinbase limits reddit transaction, the transaction's hash will change. This is known as Transaction Malleability.
They might aggregate many small inputs, or use one that is equal to or larger than the desired payment. You can copy the hex returned by getrawtransaction and paste it as a parameter to decoderawtransaction:. Thus, after a lot of effort, I had successfully created a transaction manually and had it accepted by the. She has heard about bitcoin from her techie friends and wants to start using it. Based on these mathematical functions, cryptography enables the creation of digital secrets and unforgeable digital signatures. If all goes well, Bitcoin Core is now compiled. Pooled bittrex under investigation purse.io free bitcoins is a mining approach where multiple generating clients contribute to the generation of a block, and then split the block reward according the contributed processing power. So the difficulty doesn't need to be broadcast by a central authority. Bitcoins the hard way: The contents of the transaction including the hash of the previous transaction are hashed and signed with B's private key. Signing the transaction is the hard part, as you'll see .
This result is encoded using the Base58 alphabet described previously. If an error occurs, it is most likely because of a missing or incompatible library. The private key isf19ce6e15aea35eec2e00ebd6dcffdabd9b2de4 so check that's the value you have. Do you also have a Dogecoin address? Bitcoin addresses are almost always encoded as "Base58Check" see [base58] , which uses 58 characters a Base58 number system and a checksum to help human readability, avoid ambiguity, and protect against errors in address transcription and entry. Strictly not so. Transactions "are assembled into Blocks" and broadcast to the network for mining at 10 minute intervals. With these keys they can sign transactions to unlock the value and spend it by transferring it to a new owner. Unless the wallet can aggregate inputs in such a way to exactly match the desired payment plus transaction fees, the wallet will need to generate some change. Hi RandomName!
Bitcoin is such a system, decentralized by design, and free of any central authority or point of control that can be attacked or corrupted. Find a friend who has bitcoin and buy some from him or her directly. Transaction C spends. Carefully review the build prerequisites, which are in the first part of the build documentation. Next, we will look at how keys are generated, stored, and managed. The private key k is a number, usually picked at random. Antminer s9 schematics john mcafee crypto wallet your client will receive the block and your client shows that the transaction was processed. All the miners participating in that mining pool immediately start computing Proof-of-Work for the candidate block. Finally they guarantee that there will be just one chain going forward, at least if the fork is accepted by the community. You have the gift! Structure of the example Bitcoin transaction. The secpk1 curve is defined by the following function, which produces an elliptic curve:. I added a lot of visuals which I created on paper when trying to understand how the different parts of the protocol was related. Bitcoins the hard way: Like an ant colony, the bitcoin network is a bitcoin mathematics pdf coinbase invalid code always wrong network of simple nodes following simple rules that together can do amazing things without any central coordination. Units of currency called bitcoin are japan bitcoin market macd indictor bitcoin chart to store and transmit value among participants in the bitcoin network. What does a coinbase output script look like and how would it be used to fund a transaction? The peer-to-peer network There is no centralized Bitcoin server. I waiting for. For instance, what if miners use a forced soft fork to make the inflation subsidy 50 BTC forever?
Hi, This is a very useful and valuable article. The sample transactions, blocks, and blockchain references have all been introduced in the actual bitcoin blockchain and are part of the public ledger, so you can review them on any bitcoin system. The Bitcoin network protocol allows full nodes peers to collaboratively maintain a peer-to-peer network for block and transaction exchange. Find a friend who has bitcoin and buy some from him or her directly. Cold storage is achieved when Bitcoin private keys are created and stored in a secure offline environment. These early digital currency projects issued digital money, usually backed by a national currency or precious metal such as gold. Every idea, analogy, question, answer, and explanation you find in this book was at some point inspired, tested, or improved through my interactions with the community. Furthermore, bitcoin cannot be inflated by "printing" new money above and beyond the expected issuance rate. Gox heist also adds panic to most believers that anytime, transaction malleability attack might arise. Not to be confused with consensus. I became obsessed and enthralled, spending 12 or more hours each day glued to a screen, reading, writing, coding, and learning as much as I could.
Unlike other foreign currencies, you cannot yet buy bitcoin at a bank or foreign exchange kiosk. The checksum is an additional four bytes added to the end of the data that is being encoded. I first stumbled upon bitcoin in mid Most, however, present a compromise by taking control of the bitcoin keys from users in exchange for ease-of-use. The Mt. In the following sections we will examine this transaction in more detail. Several bitcoin developers contributed code samples, reviews, comments, and encouragement. The nodes on the network exchange transactions, blocks, and addresses of other peers with each other. There is a mathematical relationship between the public and the private key that allows the private key to be used to generate signatures on messages. For the outputs,. If we compare a bitcoin transaction to a paper check, the bitcoin address is the beneficiary, which is what we write on the line after "Pay to the order of. In the post you mention hash type as one of the steps that tripped you up. This shows a node running Bitcoin Core version 0.

