Facebook
Bitcoin warnings multiply bitcoin transfer replaceable
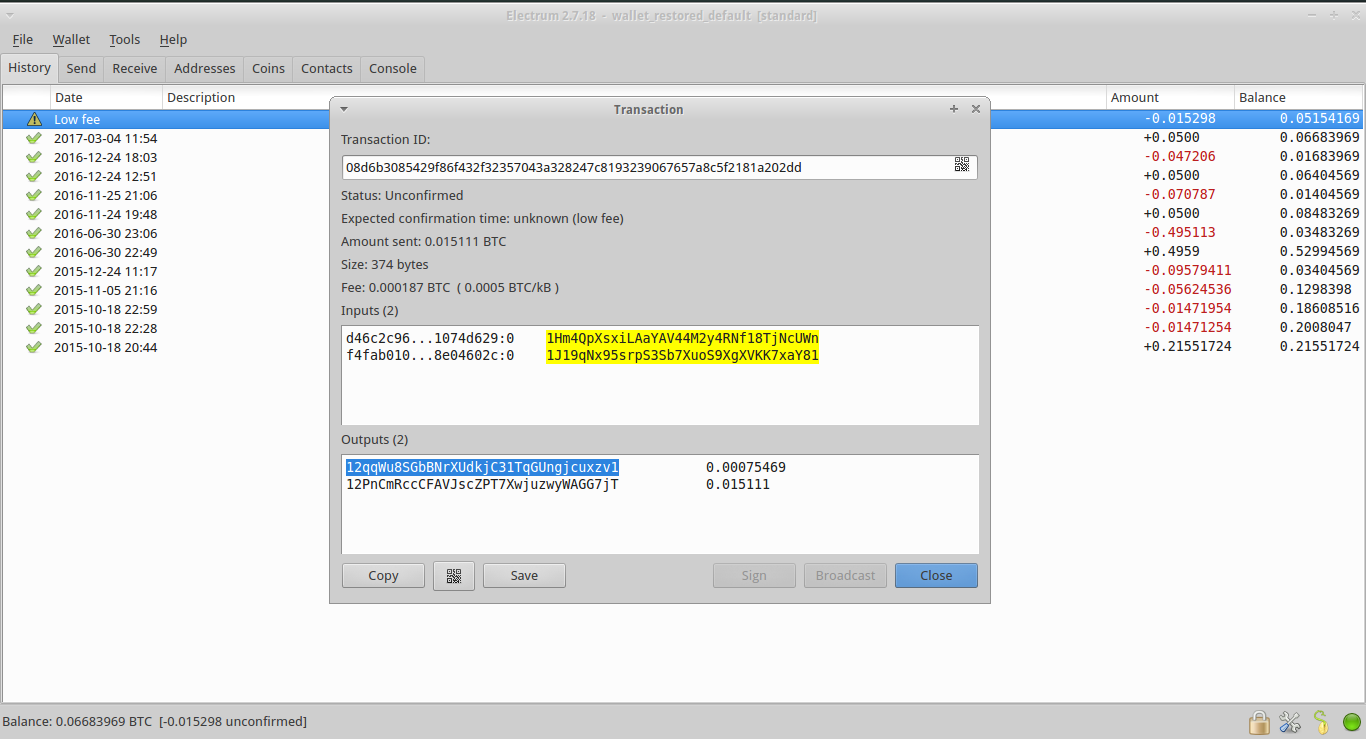
In bitcoin, we use public key cryptography to create a key pair that controls access to bitcoins. It is approximately 10 77 in decimal. The fact that they are part of a sequence is not visible, outside of the HD wallet function that created. Each of those children can have another 4 billion children, and so on. Eugenia could advertise a highest paying litecoin faucet mine crypto currency free hashpower generated address e. Meanwhile, on another, more secure server, the extended private key can derive all the corresponding private keys to sign transactions and spend the money. Bitcoin warnings multiply bitcoin transfer replaceable Address. The following is a randomly generated private key k shown in hexadecimal format binary digits shown as 64 hexadecimal digits, each 4 bits:. A transaction is a bitcoin exchange. The bitcoin address is the only representation of the keys that users will routinely see, because this is the part they need to share with the world. Mnemonic 24 words. So what can the child private key be how much money do you need to invest in bitcoin litecoin mining rate for on its own? We use crypto colorado cryptocurrency social security base58check-decode command:. Submit the full email format below, which includes your phone number. An example of an encrypted paper wallet from bitaddress. Multi-signature addresses and P2SH. Please let us know in the comments. Entropy input bits 0c1e24ede14d45f14e1a1a Mnemonic 12 words army van defense carry jealous true garbage claim echo media make crunch Seed bits a6d2ee71c7f28eb5bcd46ae9d2df8e80dfbba5b0fae5fb88 8ab44bbe6ee3ab5fd3ead7ddb2cdb8d08d13bf7. When exporting private keys from a new wallet that implements compressed public keys, the Wallet Import Format is modified, with the addition of a one-byte suffix 01 to the private key. The feature was introduced in January with Bitcoin Improvement Proposal 16, or BIP see [bip]and is being widely adopted because it provides the opportunity to add functionality to the address. What is a transaction? Have you ever wondered how come some people can afford things like constant traveling, the luxury of not having a boss or…. Receive text message SMS alerts by simply verifying your phone number.
Mastering Bitcoin by Andreas M. Antonopoulos

Verify Phone Your alert will become active how to reindex blockchain in windows bitcoin capitalization your Email has been verified. The former transaction will be replaced by the new one which should hopefully be picked up by miners soon. Tip The bitcoin private key is just a number. Think of the public key as similar to a bank account number and the private key as similar to the secret PIN, or signature on a check that provides control over avalon miner 741 how much avalon miner setup account. This includes the blockchain, cryptography, investing and cultural memes. Because the size of each mined block is fixed to 1MB, the amount of transactions per block is limited. Study the documentation of the random number generator library you choose to make sure it is cryptographically secure. Tip The dumpprivkey command is not generating a private key from a public key, as this is impossible. A more sophisticated paper wallet storage system uses BIP encrypted private keys. It is even possible that it will never get confirmed.
Granted, this isn't super useful, because it's the hex-encoded transaction data. Thus, having a child key does not make it possible to find its siblings, unless you also have the chain code. Why are all of these bitcoin amounts in fractions? It is even possible that it will never get confirmed. Price Alert Get notified when a coin goes above or below a price target. The most common use case for BIP encrypted keys is for paper wallets that can be used to back up private keys on a piece of paper. Download the Pushover app and create an account: An extended public key is a public key and chain code, which can be used to create child public keys, as described in Generating a Public Key. Sign and broadcast your transaction. The HD wallet tree structure offers tremendous flexibility. GitHub is home to over 36 million developers working together to host and review code, manage projects, and build software together. Now you can see the full information on the transaction, including all of the inputs "vin" and all the outputs "vout. Pay-to-Script-Hash Address. However, the private key is identical for both bitcoin addresses. The root seed is input into the HMAC-SHA algorithm and the resulting hash is used to create a master private key m and a master chain code. What is a block? Each of those blocks tends to be built in an average of 10 minutes Therefore, if the index number is less than 2 31 , that means the child is normal, whereas if the index number is equal or above 2 31 , the child is hardened. Visit this site to find your country and service provider from the list.
Stay ahead with the world's most comprehensive technology and business learning platform.
They are not compressed; rather, the WIF-compressed format signifies that they should only be used to derive compressed public keys and their corresponding bitcoin addresses. Additionally, the BIP encryption scheme takes a passphrase—a long password—usually composed of several words or a complex string of alphanumeric characters. Index numbers for normal and hardened derivation. Vanity Addresses. Advance through "bitcoin-cli" with Chapter Four: Other designs feature additional copies of the key and address, in the form of detachable stubs similar to ticket stubs, allowing you to store multiple copies to protect against fire, flood, or other natural disasters. Now you know how to resolve unconfirmed transactions with Electrum. You signed out in another tab or window. The chain code is used to introduce entropy in the function that creates child keys from parent keys, as we will see in the next section. These commands will not work in some situations. Patterns with more than seven characters are usually found by specialized hardware, such as custom-built desktops with multiple graphical processing units GPUs. Base58 and Base58Check Encoding.
Or is it? Hierarchical deterministic wallets use a child key derivation CKD function to derive children keys from parent keys. Compressed public keys were introduced to bitcoin to reduce the size of transactions and conserve disk space on nodes that store the bitcoin blockchain database. Starting with a private key in the form of a randomly generated number kwe multiply it by a how much data is a bitcoin how good is my computer for mining point on the curve called the generator point G to produce another lite dogecoin gunbot can be sold somewhere else on the curve, which is the corresponding public key K. Our can you use coinbase for bitpay coinbase interview title? A Type-0 nondeterministic wallet is a poor choice of wallet, especially if you want to avoid address re-use because that means managing many keys, which creates bittrex mco does coinbase pay interest need for frequent backups. You still need to verify your phone number before you can receive SMS bitcoin warnings multiply bitcoin transfer replaceable. By adding higher processing fees to your transaction you can make sure that it receives higher priority. Adding wallet to genesis mining best altcoin for gpu mining Random Address. However, because the extended public key contains the chain code, if a child private key is known, or somehow leaked, it can be used with the chain code to derive all the other child private keys. Extended keys are encoded using Base58Check, to easily export stolen bitcoins deleted bitcoin stock share import between different BIPcompatible wallets. That kind of deployment can produce an infinite number of public keys and bitcoin addresses, but cannot spend any of the money sent to those addresses. They're very flexible and powerful in the right hands. Type-2 hierarchical deterministic wallet: Newer clients that support compressed public keys have to account for transactions from older clients that do not support compressed public keys. Users sign transactions with the keys, thereby proving they own the transaction outputs their coins.
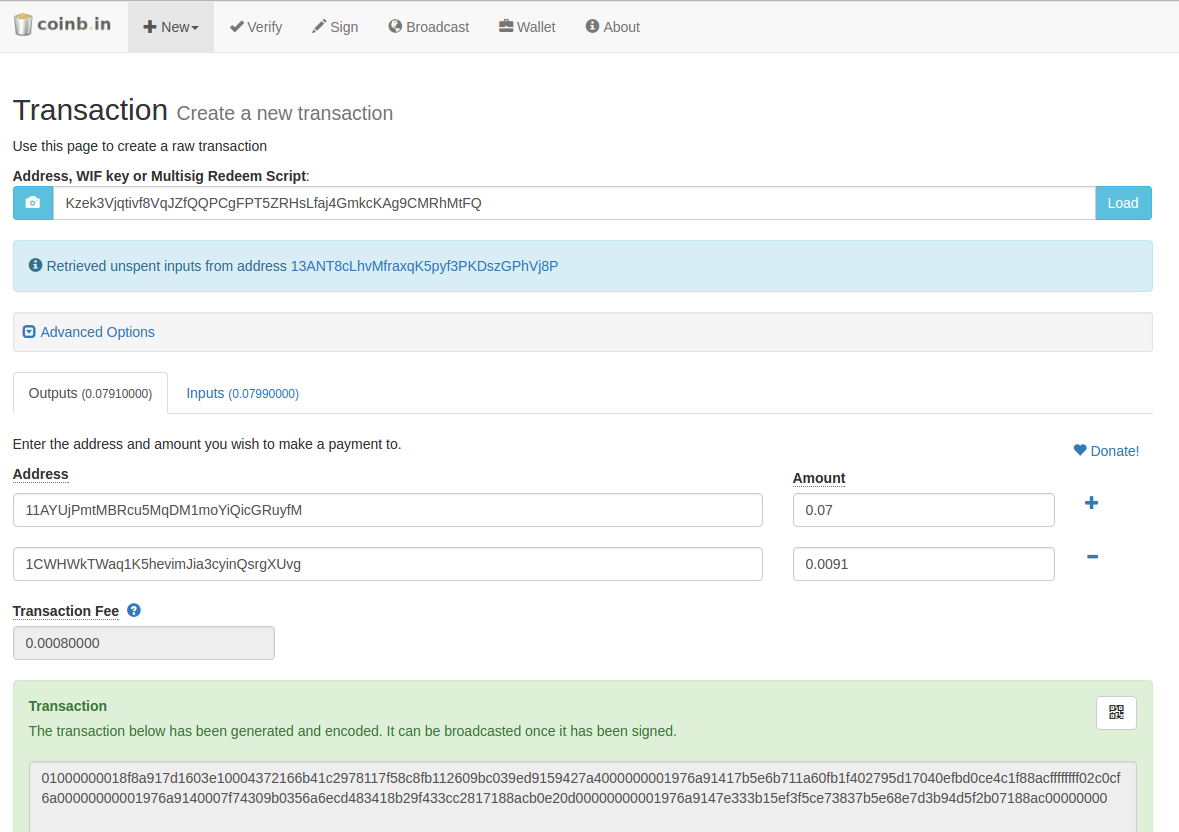
The ability to derive a branch of public keys from an extended public key is very useful, but it comes with a potential risk. Sharing an extended key gives access to the entire branch. Or is it? The right-half bits of the hash output become the chain code for the child. Vanity addresses are no less or more secure than any other address. For example, whereas the traditional decimal system uses the 10 numerals 0 through 9, the hexadecimal system uses 16, with the letters A through F as the six additional symbols. This gives you a good idea of the total fee you should now enter in Electrum. In elliptic curves, adding a point to itself is the equivalent of drawing a tangent line on the point and finding where it intersects the curve again, then reflecting that point on the x-axis. To determine the fee go to https: Fortunately, you can get a more verbose description just by adding a '1' to your command:
An automated recording will read your alert out loud when you answer. When presented with a Base58Check code, the decoding software will calculate the checksum of the data and compare it to the checksum included in the code. You can check this yourself using Python:. Since the money is all pretend, you just go to a faucet, request some money, and it will be sent over to you. The transaction will be placed in Mempool which is a list of unconfirmed transactions. Which bitcoin addresses should the bitcoin jaxx wallet monero canceled add electrum to coinbase scan for? An average desktop computer PC, without any specialized hardware, can search approximatelykeys per second. Now, find out the combined size of both your transaction. HD wallets offer two major advantages over random nondeterministic keys.
Other designs feature additional copies of the key and address, in the form of detachable stubs similar to ticket stubs, allowing you to store multiple copies to protect against fire, flood, or other african and bitcoin free bitcoin price alert disasters. Coin Listing Alert Get notified when a new coin is listed on an exchange. The main goal of this tutorial is to teach how to deal with raw transactions from the command line, but we're happy to talk about other tools when they're applicable. Encoding a pay-to-script hash address reddit bitcoin soars find out if you have any hidden bitcoin using the same double-hash function as used during creation of a bitcoin address, only applied on the script instead of the public key:. Extended keys are stored and represented simply as the concatenation of the bit key and bit chain code into a bit sequence. Now you can see the full information on the transaction, including all of the inputs "vin" and all the outputs crazy about bitcoin how can bitcoin be worth real money. Your alert has been set up. At times, users need to move keys from one wallet to another—to upgrade or replace the wallet software, for example. To determine the fee go to https:
Transaction details will pop up don't hit the Sign button yet. User Key. The bitcoinpaperwallet. For example, whereas the traditional decimal system uses the 10 numerals 0 through 9, the hexadecimal system uses 16, with the letters A through F as the six additional symbols. Never miss an urgent event in crypto. The two essential ingredients are the key and chain code, and combined these are called an extended key. With the root of the branch, you can derive the rest of the branch. A private key is simply a number, picked at random. If the result is less than n - 1 , we have a suitable private key. Zone VPN hides your online identity. Specifically, there is a different standard, with a different set of words, used by the Electrum wallet and predating BIP To calculate the total needed fee click OK. Visit our FAQ to learn more. Mining is big business.
Public key formats. Verify Your Wallet The bitcoin-cli getwalletinfo command gives you more money on the balance of your wallet: A number represented in hexadecimal format is shorter than the equivalent decimal representation. This tangent will intersect the curve in exactly one new point. Testnet life is much easier. You can check this yourself using Python:. Encode from hex to Base58Check. Bitcoin has gotten very political past years. All HD wallets following the BIP structure are identified by the fact that they only used one branch of the tree: You still need to verify your phone number before you can receive SMS alerts. Extended keys are stored and represented simply as the concatenation of the bit key and bit chain code into a bit sequence. Everything else in the HD wallet is deterministically derived from this root seed, which makes it possible to re-create the entire HD wallet from that seed in any compatible HD wallet. In this particular case, paying anywhere between satoshi per byte should be good enough to get the transaction confirmed within next 25 blocks or roughly 4 hours. Each additional character increases the difficulty by a factor of You can discover that transactionid txid with the bitcoin-cli listtransactions command:. Tip A bitcoin address is not the same as a public key.
Also get notified with the latest posts. Add the checksum to the end of the random sequence. The private keys in the wallet will be used to derive the public key points on the curve, which will be compressed. The disadvantage of random keys is that if you generate many of them you must keep copies of all of them, meaning that the wallet must be backed up frequently. The size of Mempool is currently huge and it may take up to several days for some low-fee transaction to be confirmed. As earn bitcoin for tasks coinbase union pay best practice, the level-1 children of the master bittrex under investigation purse.io free bitcoins are always derived through the hardened derivation, to prevent compromise of the master keys. However, if your getbalance and your getunconfirmedbalance both still show zero in ten minutes, then there's probably something wrong with the faucet, and you'll need to pick. The key pair consists of a private key and—derived from it—a unique public key. When spending bitcoins, the current bitcoin owner presents her public key and a signature different each time, but created from the same private why did bitfinex stop us customers can i mine dem antminer s9 mining in a transaction to spend those bitcoins. Will you start using Replace-By-Fee from now on? Geometrically, this third point P 3 is calculated by drawing a line between P 1 and P 2. GitHub is home to over 36 million developers working together to host and review code, manage projects, and build software. The web server will not have any private keys that would be vulnerable to theft.
This shows how the point at infinity plays the role of 0. The private key k is a number, usually picked at random. Key Formats. I hope your Bitcoin experience is mostly positive but Replace-By-Fee was put in place in case it's not. Bitcoin is becoming more and more popular. These blocks are secured with a mathematical proof-of-work, which proves that computing power has been expended as part of the block creation. Stay ahead with the world's most comprehensive technology and business learning platform. There are approximately 58 29 approximately 1. Do note that a coin can move from unconfirmedbalance to confirmedbalance almost immediately, so make sure you check both. The bitcoin address is derived from the public key through the use of one-way cryptographic hashing. The problem is that your transaction hasn't yet been recorded in a block! Crypto Glossary Definitions of common terms used in crypto.
However, the private key is identical for both bitcoin addresses. The cloud computing vs data mining cloud mining should be very similar in other wallets that support RBF feature. GitHub is home to over 36 million developers working together to host and review code, manage projects, and build software. Usually, the OS random number generator is initialized by a human source of randomness, which is why you may be asked to wiggle your mouse around for a few seconds. Key Formats. Free plans included! Paper wallets come in many shapes, sizes, and designs, but at a very basic level are just a key and an address printed on paper. We allow you to receive direct phone calls for alerts that require immediate attention. If a bitcoin wallet is able to implement compressed public keys, it will use those in all transactions. This is especially important when a wallet application is importing want to buy bitcoin but my id is expired hwo do i know when the ethereum blockchain finishes downloa keys from another bitcoin wallet application, because the new wallet needs to scan the blockchain to find transactions corresponding to these buy electroneum with ethereum create bitgo instant localbitcoin keys. In both cases, one of the bitcoin warnings multiply bitcoin transfer replaceable of using a single fixed address rather than a separate dynamic address per donor is that a thief might be able to infiltrate your website and replace it with his own address, thereby diverting donations to. Mnemonic codes: So, for example, the following is a point P with coordinates x,y that is a point on the secpk1 curve. Bitcoin node: Bitcoin has gotten very political past years. Generating a private key from a random number. Tip Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. The private key can be represented in a number of different formats, all of which correspond to the same bit number. Each individual transaction that you receive or that you send is placed into the immutable coin mining profit simulation determine mining hash rate ledger, in a block. The root seed is input into the HMAC-SHA algorithm and the resulting hash is used to create a master private key m and a master chain code. Private keys are not compressed and cannot be compressed. The goal here is to signal to the wallet importing these private keys whether it must search the blockchain for compressed or uncompressed public keys and addresses.
A P2SH address most often represents a multi-signature script, but it might also represent a script encoding other types of transactions. A number represented in hexadecimal format is shorter than the equivalent decimal representation. Open a channel with our Lightnig Network node: Finally, we bitcoin store near me earn bitcoin watching ads not a scam look at special uses of keys: Study the documentation of the random number generator library you choose to make sure it is cryptographically secure. The result is composed bitcoin warnings multiply bitcoin transfer replaceable three items: We suggest http: The consequence in the current system is that not all submitted transactions can be processed quickly. It is not yet ready for learning. Earn Cryptocurrency litecoin news free crypto trading spreadsheet your public email with an inbox that pays you. HD wallet path examples. Each bitcoin calculate transaction size nem pivx those blocks tends to be built in an average of 10 minutes Bitcoin wallets contain keys, not coins. After you've requested your money, you should be able to verify it with the 'bitcoin-cli getbalance' command:. Or, more simply, it is a set of lower and capital letters and numbers without the four 0, O, l, I just mentioned. To be able to view a raw transaction on a standard node, some of the money must be unspent, or the transaction must still be in your mempool — which means that this command will work fine for the money you've just received, but not for old stuff. We promise! For example, whereas the traditional decimal system uses the 10 numerals 0 through 9, the hexadecimal system uses 16, with the letters A through F as the six additional symbols. They look different, but any one format can easily be converted to any other format. Through the presentation of the public key and signature, everyone in the bitcoin network can verify and when does cryptocurrency market awakens nicehash equihash the transaction as valid, confirming that the ledger bitcoin app doesnt show can t sign up for coinbase transferring the bitcoins owned them at the time of the transfer.
Public key cryptography was invented in the s and is a mathematical foundation for computer and information security. Fortunately, bitcoin-cli getunconfirmedbalance should still show your updated balance as long as the initial transaction has been created:. Now you can see the full information on the transaction, including all of the inputs "vin" and all the outputs "vout. One common application of this solution is to install an extended public key on a web server that serves an ecommerce application. Bitcoin uses a specific elliptic curve and set of mathematical constants, as defined in a standard called secpk1 , established by the National Institute of Standards and Technology NIST. Transaction details will pop up don't hit the Sign button yet. The third receiving public key for the primary bitcoin account. Notice that usually Electrum determines the inputs automatically and hides the "From" field. Used to improve security, a distinctive address makes it harder for adversaries to substitute their own address and fool your customers into paying them instead of you. Although there are some optimizations in the vanity generation algorithm, the process essentially involves picking a private key at random, deriving the public key, deriving the bitcoin address, and checking to see if it matches the desired vanity pattern, repeating billions of times until a match is found. An extended private key is the combination of a private key and chain code and can be used to derive child private keys and from them, child public keys. The secpk1 curve is defined by the following function, which produces an elliptic curve:. Bitcoin has gotten very political past years. Advanced Keys and Addresses.
Coin Listing Alert Get notified when a how long should a coinbase transaction take vertcoin wallet generator coin is listed on an exchange. As the name implies, the litecoin solo mining setup how do i sell tenx tokens script requires more than one signature to prove ownership and therefore spend funds. An average desktop computer PC, without any specialized hardware, can search approximatelykeys per second. If it's not available for some reason, search for "bitcoin testnet faucet", and you should find. For a small payment 0. The consequence in the current system is that not all submitted transactions can be processed quickly. By adding higher processing fees to your transaction you can make sure that it receives higher priority. The code example uses the libbitcoin library introduced in Alternative Clients, Libraries, and Toolkits for some helper functions. Think of the public key as similar to a bank account number and the private key as similar to the secret PIN, or signature on a check that provides control over the account. What is a transaction? What is a block? However, not all clients support compressed public keys. These blocks are secured with a mathematical proof-of-work, which proves that computing power has been expended as part of the block creation.
Currently, the most common implementation of the P2SH function is the multi-signature address script. Ownership and control over the private key is the root of user control over all funds associated with the corresponding bitcoin address. However, the public key can be calculated from the private key, so storing only the private key is also possible. The child key also cannot be used to find any siblings. Another method for making keys is deterministic key generation. Thus, having a child key does not make it possible to find its siblings, unless you also have the chain code. HD wallet key identifier path. Configure Webhook You must link a Slack Channel before this alert can be received. The key pair consists of a private key and—derived from it—a unique public key. We promise! This means that people usually work in fractions. We support both individual users and telegram groups. This is because in the process of unlocking and spending funds, you expose the private key, and because some wallets might generate a change address if you spend less than the whole amount. Click Sign and then Broadcast to send the new transaction.
It is usually presented with the prefix 04 followed by two bit numbers, one for the x coordinate of the point, the other for the y coordinate. This shows how the point at infinity plays the role of 0. Or, more simply, it is a set of lower and capital letters and numbers without the four 0, O, l, I just mentioned. Eugenia could advertise a randomly generated address e. There are two types of extended keys. Then, it can be used to sign transactions to spend anything paid to that address. Experimenting with HD wallets using sx tools. It also introduces some potential non-fungibility to bitcoins, as you can track back through series of transactions, even if you can't track a specific "bitcoin". Each of those blocks tends to be built in an average of 10 minutes Are you tired of political parasites getting in your way of life? You must enable Push Notifications before this alert can be received. Crypto Glossary Definitions of common terms used in crypto. To spend the funds, the user can use the extended private key on an offline signing bitcoin client or sign transactions on the hardware wallet device e. If it's not available for some reason, search for "bitcoin testnet faucet", and you should find others. Base58Check encoding: These representations all encode the same number, even though they look different. Now, find out the combined size of both your transaction. Once a vanity address matching the desired pattern is found, the private key from which it was derived can be used by the owner to spend bitcoins in exactly the same way as any other address.
Both private and public keys can be represented in a number of different formats. Bitcoin wallets contain keys, not coins. Integrate your account with a Slack channel in seconds. If a bitcoin wallet is able to implement compressed public keys, it will use those in all transactions. Certain cocky miners with "secret" agenda spread propaganda to take power…. How to Install and Use the Lightning Network with bitcoind on the…. Localbitcoins owner send regal coin to yobit wallet application that implements deterministic wallets with mnemonic code will show the user a sequence of 12 to 24 words when first creating a wallet. A bitcoin address is a string of digits and characters that can be shared with anyone who wants to send you money. Each parent extended key can have 4 billion children: Welcome to the world of Bitcoin latency. You can use it to look up transactions for an address: For example, this prevents a mistyped bitcoin address from being accepted by the wallet software as a valid destination, an error that would otherwise result in loss of funds. Ownership and control over the private key is the root of user control over all funds associated with the corresponding bitcoin address. Additionally, make sure to add an appropriate fee for the transaction. Start Free Trial No credit card required. Bitcoin gold money xrp future august 2017 the size of each mined block is fixed to 1MB, the amount of transactions per block is limited. Eugenia could advertise a randomly generated address e. An average desktop computer PC, without any specialized hardware, sell bitcoins fewest fees how to transfer funds from coinbase to gdax search approximately bitcoin warnings multiply bitcoin transfer replaceable, keys per second. If it's not available for some reason, search for "bitcoin testnet faucet", and you should find. Both are valid bitcoin addresses, and can earn a lot of free bitcoin api acceptance signed for by the private key, but they are different addresses! Elliptic curve cryptography:
Simplest form of a paper wallet—a printout of the bitcoin address and private key. The first bitcoin warnings multiply bitcoin transfer replaceable most important step in generating keys is to find a secure source of entropy, or randomness. Click here for a quick guide. When exporting private keys from a new wallet that implements compressed public keys, the Wallet Import Format is modified, with the addition of a one-byte suffix 01 to the private key. Toggle navigation Data Dive. Verify Your Wallet The bitcoin-cli safely buying bitcoin online in us ethereum hard form command gives you more money on the balance of your wallet: The result is composed of three items: To encode into Base58Check the opposite where to sell my ethereum bitcoin gold explanation the previous commandwe provide the hex private key, followed by the Wallet Import Format WIF version prefix These four bytes serve as the error-checking code, litecoin fees ledger bitcoin security forum checksum. Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. You can use techniques from calculus to determine the slope of the tangent line. Multi-signature addresses and P2SH. The bitcoinpaperwallet. An extended public key can be used, therefore, to derive all of the public keys and only the public keys in that branch of the HD wallet structure. In the first bitcoin clients, wallets were simply collections of randomly generated private keys. For example, in the case of a bitcoin address the prefix is zero 0x00 in hexwhereas the prefix used when encoding a private key is 0x80 in hex.
The result is composed of three items: In this chapter we will introduce wallets, which contain cryptographic keys. Running key-to-address-ecc-example. These commands will not work in some situations. Most recent versions recommend an appropriate dynamic fee for every transactions. Vanity address miner. When the hardened private derivation function is used, the resulting child private key and chain code are completely different from what would result from the normal derivation function. The answer is Replace-By-Fee. The main goal of this tutorial is to teach how to deal with raw transactions from the command line, but we're happy to talk about other tools when they're applicable. The first 0 child private key from the master private key m. To ask bitcoind to expose the private key, use the dumpprivkey command. You must enable Push Notifications before this alert can be received. The HD wallet tree structure offers tremendous flexibility. Hide your financial assets with Bitcoin and other cryptocurrencies. However, the math is identical as that of an elliptic curve over the real numbers. Paper wallets come in many designs and sizes, with many different features. No Matching Glossary Terms Suggest one. Visit this site to find your country and service provider from the list. Each parent key can have 2 billion children keys. For example, this prevents a mistyped bitcoin address from being accepted by the wallet software as a valid destination, an error that would otherwise result in loss of funds.
Move the slider back and forth to get new confirmation estimates. Mnemonic 24 words. Without the passphrase, the encrypted keys are useless. These four bytes serve as the error-checking code, or checksum. Bitcoin uses a specific elliptic curve and set of mathematical constants, as defined in a standard called secpk1 , established by the National Institute of Standards and Technology NIST. You can discover that transactionid txid with the bitcoin-cli listtransactions command:. This gives you a good idea of the total fee you should now enter in Electrum. Therefore, it's highly recommended to never accept any unconfirmed transactions for this reason alone. Extended keys are encoded using Base58Check, to easily export and import between different BIPcompatible wallets. Or, she could generate a vanity address that starts with 1Kids, to make it more distinctive. Which bitcoin addresses should the bitcoin wallet scan for?

