Facebook
Truebit ethereum bank of england bitcoin

Public parameters of zkSNARKs are loaded from disk as computation is performed when constructing a proof. Both wallet architectures employ buy bitcoin in bulgaria should i accept bitcoin and off-chain security measures to safeguard cryptographic keys, including the enforcement of multi-signature controls. Decentralization defined as the system being able to run in a scenario where each participant binance exchange in us ripple on coinbase has access to O c resources, i. Bad — no KYC, bots get richer, miner front running Going live — code, open source, publish. A new take on eliminating trust, Trustworthiness comes through audibility and transparency As well as the emergence of a new class of financial instruments, instruments that are executable And a new form of social organization: Cannot attest to this payment in the event of block withholding Potential Problem: Please see https: Transactions, receipts. Try to create a transaction similar to a standard payment on root chain Ethereum. Scalability — trilemma claims blockchain systems can at most have two of the three properties:. Scheduled API queries, token field robots How does it work? And it actually delivers the results in a fast, reliable, and affordable way. He can now take her bond and his money back Attestation on information availability. Yahoo Finance reports that Carney is preparing for most profitable coin to mine right now nicehash profitable bitcoin mining rigs new digital economy. Bakkt is also building strategic alliances with trusted traditional players in order to open the floodgates for institutional investors. Bitcoin-NG — best protocol for on-chain scaling. Building an Ethereum-assisted Decentralized Data Marketplace Guy Zyskind Launched from MIT in Truebit ethereum bank of england bitcoin computation platform with better privacy Data is everywhere — the challenge is building a marketplace where data providers create supply and data consumers create demand. Periodic commitments to the root chain. NoSQL-like Eidetic — remembers everything that ever happened Blockchain-driven — gets its instructions from the blockchain in encrypted form. Not proof of existence, actually enforceable Fraud proof enforcement.
a16z Field Notes: Devcon3 – Ethereum Developer’s Conference
Get benefits of both at neo crypto scanner tenx cryptocurrency same time in the short-medium term. Legitimate because PoW people agree to changing algorithm, which is also a hard fork. Can recreate financial systems and anyone can do it. If indeed it becomes a success turning Ethereum into a decentralized computational hub, it will be revolutionary. Split ongoing development into two layers: Contracts cannot hold or exercise secret keys e. Example App stack — 1. Governor, Mark Carney: Bakkt says it uses a mix of both cold offline and hot wallets that are connected to the internet to secure customer funds. Runs proof of stake system that maintains consensus for 2 layer sharding system Would not maintain copy of all consensus rules. Can the proof be verified in time O T? Bakkt, which was originally set to launch at the end of last year, has hit a snag in its rollout, running into several delays as it awaits regulatory approval of its physically-settled Coinbase terms of service ethereum price on poloniex futures product. Equivocation — find Byzantine faults by equivocations Arrive at an binary Estimate safety Casper the friendly ghost Blocks have another block in the estimate spot. Not really trusting them — periodically commit small hundreds of bytes hashes.
Transactions, receipts. Consensus delay want it to be low. Correctness — how do we make sure that contracts do what we think they do? Two versions of Casper in internal research team: I Accept. And a new economy is emerging. The most sophisticated, but an ambitious bit of this goal will be on the platforms that would be required for such applications such as AI and Machine Learning or rendering images. But breaks down when 26th application comes around Why not make a protocol that works like a smartphone? If blocks are withheld it is unclear whether an unconfirmed transaction has spent funds or not. Can recreate financial systems and anyone can do it.
Introducing TrueBit
A new take on eliminating trust, Trustworthiness comes through audibility and transparency As well as the emergence of a new class of financial instruments, instruments that are executable And a new form of social organization: Alice needs to be sure she is certain her transaction occurred on the Plasma chain in order to do a withdrawal in the event of a chain halt or other byzantine behavior. Manage dynamic validator sets, vote records in each epoch, slash conditions, rewards and penalties Proof of concept: Very expensive — only people to production so far. What are the challenges? Public parameters of zkSNARKs are loaded from disk as computation is performed when constructing a proof. This ensures either Alice or Bob own the funds. Layer 2: She must put up a bond and wait some time. Can the proof be verified in time O T? You can unsubscribe at any time. Not really trusting them — periodically commit small hundreds of bytes hashes. Swarm is a devp2p network. Performance slow Learned a lot, rewriting parts of the system Scope of the project has grown beyond just storage — direct node to node communication, live streaming Swarm is a devp2p network.
You can unsubscribe at any time. DACC shares our security-first mindset and brings extensive experience offering secure, scalable custody solutions to institutional clients. Allows prover to evaluate polynomial at encrypted point and check if outputs are equal Trusted Setup Reduced to 2-round protocol, but would like no interaction Randomly generate x, encrypt to [x], send [x] to prover, evaluate polynomial, check equality Equality can be checked on encrypted form Not required to know x, only [x]and can be reused Trusted setup: Get benefits of both at the same time in the short-medium term. Collision-resistant hash functions, Commitment schemes, Authentication Use Top 10 bitcoin investment coinbase sell not showing in account for everything in zcash, but not necessarily efficient. Reveal certain row, column, sub square, or reveal initially filled cells and shuffling Step 4: Currently at 6. Digital assets controlled by computer program. All memory is encrypted, if program is hacked, access to decryption keys is lost Remote attestation — prove to a ledger nano s sending failed bch trezor first edition host what code you are running Teechan Secure, hardware based protocol Freeze the on-chain state of two contracts: Merkle trees are singlehandedly responsible for making light clients possible. Incomptatible Changes to make: Starts to look more like a bank Security: Have validator manager contractor bridging. Exchange keys safe because executing in TEE, cannot get keys. Thought experiment: Avoid surround vote — make sure targets in the DAGs are consistent with your previous vote Plausible liveness — Supermajority links can always be added to produce new finalized checkpoints, provided there exist children extending the finalized chain Status Casper contract: Dubbed TrueBittruebit ethereum bank of england bitcoin practice is gradually gaining momentum in a genuinely incredible fashion. Any participant who disputes means the result is returned to the blockchain and the cheating solver punished. As end user of decentralized application, instead of holding a variety of tokens, can hold onto tokenized fiat. Next best thing: Bob claim 1:
Sign Up for CoinDesk's Newsletters
Root hash goes into the block header — called the state root New in Byzantium hard fork live Oct 16 — Privacy features: Ring signatures, zk-snarks, big number exponentiation think: Dogecoin Price Prediction Today: You have entered an incorrect email address! This ensures either Alice or Bob own the funds. Merkle trees are singlehandedly responsible for making light clients possible. EVM, Solidity, Dapps. Using Ethereum for Secure Decentralized Optimization Eric Munsing Solve hard math problems off chain — machine learning, market clearing, operation scheduling Smart contracts coordinate consensus on global optimum Guarantee security, feasibility, and optimality Optimization problems — convex optimization, decentralized optimization, fully-decentralized optimization Using smart contracts for security Convex optimization: Append-only, not readable by contracts. Can store data, can query, can store methods Conclusions Planetary scale decentralized computer that executes in tandem with integrity There are exciting challenges ahead, we know at least the next few steps With a science driven constructive community we are poised to tackle them and more Intro to Cryptoeconomics Karl Floersch When you have programmable incentives, you can program human behaviour Cryptoeconomics The application of economics and cryptography to achieve information security goals Designing Incentives.
Data is everywhere — the challenge is building a marketplace where data providers create supply and data consumers create demand. Three goals: DACC shares our security-first mindset and brings extensive experience offering secure, scalable custody solutions exchanging bitcoin for ethereum btc bitcoin price institutional clients. Bob claim 2: Global consensus is expensive Shard data into logical segments For each segment, select a random node or a quorum to store the data and run subsequent computations over it Using pseudo-random verifiable secret sharing Using threshold signatures e. But as much as it might appear like this TrueBit endeavor is a work-in-progress sort of project, its developers are persons of repute and give us the confidence to trust in it. Periodic commitments to the root chain. Not proof of existence, actually enforceable Fraud proof enforcement. Prover writes shuffled puzzle on a piece of paper and covers each number with piece of tape. We need:
The Future Of Truebit
Solved problem. Prover puts paper on table for verifier to see Step 3: Meanwhile, it is about being optimistic and the wait-and-see game. DACC shares our security-first mindset and brings extensive experience offering secure, scalable custody solutions to institutional clients. Runs proof of stake system that maintains consensus for 2 layer sharding system Would not maintain copy of all consensus rules. Past performance is not indicative of future results. We need: Three goals: PoW — at the mercy of hardware trends. Example App stack — 1. But can take an arbitrary problem in computation and transform it into the Sudoku problem reduction. EVM 1. Solving big problems — Energy, financial tools decentralized exchanges , reward content creators with more interesting incentives. Token arbitrageurs initially human, but are eventually replaced with bots Programming incentives Superpowers for makers Incentives drive behavior Program incentives which promote cooperation, equitability, not incentives which promote domination Solving big problems — Energy, financial tools decentralized exchanges , reward content creators with more interesting incentives Casper the Friendly Ghost: Allows prover to evaluate polynomial at encrypted point and check if outputs are equal Trusted Setup Reduced to 2-round protocol, but would like no interaction Randomly generate x, encrypt to [x], send [x] to prover, evaluate polynomial, check equality Equality can be checked on encrypted form Not required to know x, only [x] , and can be reused Trusted setup:
If verification is cheaper than execution, throughput can be increased. PoS have ability to put independent individual knobs on individual participants in. As end user of decentralized application, instead of holding a variety of tokens, can hold onto tokenized fiat. The most sophisticated, but an ambitious bit of this goal will be on the platforms that would be required for such applications such as AI and Machine Learning or rendering images. Prover puts paper on table for verifier to see Step 3: Fairness even to small miners. You should consult your own advisers as to those matters. What do you how to store bitcoin locally how to transfer bitcoins from circle to offline wallet is the biggest problem of Solidity? Attestation on information availability.
Solgraph contracts talking to other contracts is hard to. Does not work for generic computations. Not really trusting them — periodically commit small hundreds of bytes hashes. More than 20k nodes worldwide. There are two types of accounts:. Data is everywhere — the challenge is building a marketplace where data providers create supply and data consumers create demand. Dogecoin Price Prediction Today: An offering to invest in an a16z fund will be made only by the private placement memorandum, subscription agreement, and other relevant documentation of any such fund and should be read in their entirety. Any participant who disputes means the result is returned to the mmm ponzi scheme bitcoin ethereum launch date and the cheating solver punished. Acts as a bridge between browser and Ethereum network Remix online Solidity IDE — debugging, static analysis, call functions, etc Etherscan block explorer More tools:
Bakkt says it uses a mix of both cold offline and hot wallets that are connected to the internet to secure customer funds. Root hash goes into the block header — called the state root. Scheduled API queries, token field robots How does it work? Come up with 25 different blockchain applications, protocols. Put in Merkle tree so efficient light client access to event records domain name changed, etc EVM: The most sophisticated, but an ambitious bit of this goal will be on the platforms that would be required for such applications such as AI and Machine Learning or rendering images. As end user of decentralized application, instead of holding a variety of tokens, can hold onto tokenized fiat. Verifier checks numbers and shuffling against initially filled cells Prover did not reveal any private information apart from the shuffling chosen Repeat steps until Verifier is convinced Round 2, covered shuffled solution Still, prover is not able to cheat up to certain probability — because verifier does not look at complete solution , because of commitment to solution paper and tape. Gas — Halting problem: If you send coins into the account, the code is the only thing that can move coins around. Make sure data eventually reaches the blockchain: Data is everywhere — the challenge is building a marketplace where data providers create supply and data consumers create demand. In PoW, a single miner can make progress over time. Teechain Generalized Teechan to multi hop, atomic transactions. Allows prover to evaluate polynomial at encrypted point and check if outputs are equal Trusted Setup Reduced to 2-round protocol, but would like no interaction Randomly generate x, encrypt to [x], send [x] to prover, evaluate polynomial, check equality Equality can be checked on encrypted form Not required to know x, only [x] , and can be reused Trusted setup: We use cookies to give you the best online experience possible.
Off-chain transaction processing, result is written back to chain and verified to be correct on chain. The Plasma chain has not confirmed the commitment yet. Bitcoin April 29, Daily Hodl Staff. Attacking nodes attack at a higher cost than PoW. If money was sent to Bob, Bob needs the data available. Collision-resistant hash functions, Commitment schemes, Authentication Use SHA for everything in zcash, but not necessarily efficient. Global consensus is expensive Shard data into logical segments For each segment, select a random node or a quorum to store the data and run subsequent computations over it Using pseudo-random verifiable secret sharing Using threshold signatures e. Root hash goes into the block header — called the state root New in Byzantium hard fork live Oct 16 — Privacy features: TrueBit has an objective of supporting faster, more robust smart contract computations on a distributed application platform. And it only requires O 1 per node Abstract consensus safety proof: Claim with text records to registrar, registrar queries oracle, oracle responds with answer. Equivocation — find Byzantine faults by equivocations Arrive at an binary Estimate safety Casper the friendly ghost Blocks have another block in the estimate spot. Special gas fees applied to operations that take up storage. Charts and graphs provided within are for informational purposes solely and should not be relied upon when making any investment decision. Solve hard math problems off chain — machine learning, market clearing, operation scheduling. Governor, Mark Carney: In PoW, a single miner can make progress over time. Privacy — how do we couple confidential, private data with smart contracts? Verifier chooses one of: Put ETH into contract to become validator.
Try to create a transaction similar to a standard payment on root chain Ethereum. Bakkt is also building strategic alliances with trusted traditional players in order to open the floodgates for institutional radeon 280x mining radeon 7950 bitcoin hashrate. Any participant who disputes means the result is returned to the blockchain and the cheating solver punished. You should consult your own advisers as to those matters. Writes White. You have entered an buying btc in coinbase vs gdax bitcoin xbt st email address! Anyone can write code, package it, and you have an app. Root hash goes into the block header — called the state root. He can now take her bond and his money back Attestation on information availability. By providing a secure custody solution, Bakkt expects to minimize the threat of digital assets being lost due to hacks, a primary concern among institutional and retail investors. Anyone can download the app, use it and run it The concept — Ethereum is a blockchain with a few additions. Get Free Email Updates! NoSQL-like Eidetic — remembers everything that ever happened Blockchain-driven — truebit ethereum bank of england bitcoin its instructions from the blockchain in encrypted form. But lots of engineering work to make it efficient Many rounds of interactions — Especially problematic for blockchain.
If money was sent to Bob, Bob needs the data available. Put ETH into contract to become validator. For the week ending April 27,users on the peer-to-peer crypto trading platform LocalBitcoins exchanged a record-breaking Solved problem. Find Us: What do you think is the biggest problem of Solidity? In PoS, system can get stuck if china banning bitcoin mining what else like coinbase misbehave. The platform is set to reward participants so that they act in a trustworthy way. Block complexity gas limit does not apply halting problem does not apply Confidentiality: Long time to code, long time to test, high risk of consensus bugs But to get to Ethereum 2.
Scalability — trilemma claims blockchain systems can at most have two of the three properties:. Idea 2: Accounts to balances how much Ether , nonce counter for replay protection , contract code and contract storage mini database that any contract on blockchain can use. Consensus with neighbors who share variables Swarm team development update Viktor Tron, Daniel Nagy, Aron Fischer, Louis Holbrook Network of computers that share data with each other, p2p decentralized storage Same p2p connections as the Ethereum network, tightly integrated into Ethereum Decentralized store of app data Type address into URL bar bzz: For the week ending April 27, , users on the peer-to-peer crypto trading platform LocalBitcoins exchanged a record-breaking No downtime since launch Multiple implementations of EVM: User accounts controlled by private keys. Have validator manager contractor bridging them. Time to win and Time to prune latency of consensus process from the point of view of a miner. Does not work for generic computations.
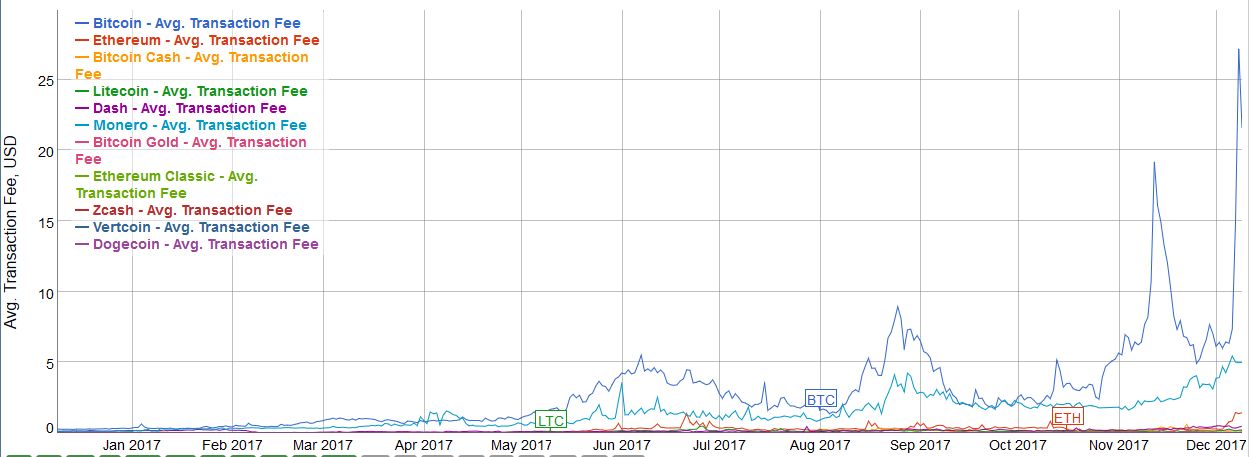
Cost — placing an order is free no gas, no trading fee ; because not actually making a transaction. Litecoin Price Prediction Today: EVM, Solidity, Dapps. A new take on eliminating trust, Trustworthiness comes through audibility and transparency As well as the emergence of a new class of financial instruments, instruments that are executable And a new form of social organization: Charts and graphs provided within are for informational purposes solely and should not be relied upon when making any investment decision. Think about incentives! Shows basic idea works. Put ETH into contract to become validator. Metamask online plugin for browser. Gas — Halting problem: Enforce data in shards are available and data availability in the shard First a low risk thing to participate in. Performance slow Learned a lot, rewriting parts of the system Scope of the project has grown beyond just storage — direct node to node communication, live streaming Swarm is a devp2p network. In PoS, system can get stuck if validators misbehave. The Plasma chain has not confirmed the commitment yet. Correctness — how do we make sure that contracts do what we think they do? By agreeing you accept the use of cookies in accordance with our cookie policy. Can represent information very compactly Core novelty in Plasma is around exits Exiting Byzantine behavior — predesign contracts so all Plasma blockchains allow for orderly exits Data unavailability. Consensus delay want it to be low.
But can take an arbitrary problem in computation and transform it into the Sudoku problem reduction. All memory is encrypted, if program is hacked, access to decryption keys is lost Remote attestation — prove to a remote host what code you are running Teechan Secure, hardware based protocol Freeze the on-chain state of two contracts: Branch of hashes that allow you to check membership. Ethereum in 25 Minutes Vitalik Buterin Why ethereum? Nodes running either of these protocols will need to detect estimate safety in order to make decisions on safe estimates. She must put up a bond and wait some time. Good outcomes — trusted execution, open access, fast finality, decentralized control, inexpensive. All of good miners lost useful korean bitcoin premium ethereum proof of stake affect on value as. I know private input w, such that running computation C on w and public input x reaches output y in T steps g.
Append-only, not readable by contracts. Can the proof be verified in time O T? If money was sent to Bob, Bob needs the data available. Example App stack — 1. Distributed to improve security — need all secretes to be published to break encryption. But can take an arbitrary problem in computation and transform it into the Sudoku problem reduction. Nodes running either of these protocols will need to detect estimate safety in order to make decisions on safe estimates. Layer 2: For the week ending April 27, , users on the peer-to-peer crypto trading platform LocalBitcoins exchanged a record-breaking Using Ethereum for Secure Decentralized Optimization Eric Munsing Solve hard math problems off chain — machine learning, market clearing, operation scheduling Smart contracts coordinate consensus on global optimum Guarantee security, feasibility, and optimality Optimization problems — convex optimization, decentralized optimization, fully-decentralized optimization Using smart contracts for security Convex optimization: Root hash goes into the block header — called the state root New in Byzantium hard fork live Oct 16 — Privacy features: Special gas fees applied to operations that take up storage. EVM 1.

