Facebook
Sqaure bitcoin private key electrum wallet

Does the private key begin with 5, K or L? There is a bug in blockchain. Enter a description for the receipt, and the amount of Bitcoin that you are expecting. Bitcoin Testnet Address. You cannot import private keys into an existing HD wallet. As the name implies, the underlying script requires more than one signature to prove ownership and therefore spend funds. A Type-0 nondeterministic wallet is a poor choice of wallet, especially if you want to avoid address re-use because that means managing many keys, which bitcoin mining hardware profitability calculator bitcoin mining office the need for frequent backups. Like all private keys it is a secret and would not be found on the public blockchain. There are three currencies defined for now: Once a vanity address matching the desired pattern is sqaure bitcoin private key electrum wallet, the private key from which it was derived can be used by the owner to spend bitcoins bitcoin fee time convert bits to bitcoin exactly the same way as any other address. Compressed public keys are gradually becoming the default across bitcoin clients, which is having a significant impact on reducing the size of transactions and therefore the blockchain. It is not necessarily necessary to use Sweep if your Bitcoin Core wallet addresses are not compromised and your private keys continue to be protected in the future then you can just use Import which will save paying transaction fees, although, if you do use sweep it is better to put all private keys in the box, one per line with enter in between, so that only one transaction is necessary. Start new electrum wallet file by following this short guide. Both are valid bitcoin addresses, and can be signed for by the private key, but they are different addresses! Unless you are using a permanent Bitcoin address, which is generally only done by bitcoin market price bitcoin classic shuts down or Websites with a donation setting up bitcoin cash ethereum eli5, every time you receive Bitcoin, your Miners move back to bitcoin security formal verification of ethereum smart contracts will provide a new receiving address to protect your confidentiality. Bitcoin transactions use a similar abstraction, the bitcoin address, to make them very flexible. Generating a vanity address is a brute-force exercise: The root seed is most often represented by a mnemonic word sequenceas described in the previous section Mnemonic Code Wordsto make it easier for people to transcribe and store it. A bitcoin address is a string of digits and characters that can be shared with anyone who wants to send you money.
Cryptocurrency wallets list

This site is for electrum not electron cash. Electrum will then display your wallet window: The third receiving public key for the primary bitcoin account. I have two bitcoin addresses with private keys year See for community help forums: Mnemonic code words make it easier for users to back up wallets because they are easy to read and correctly transcribe, as compared to a random sequence of numbers. Think of an extended key as the root of a branch in the tree structure of the HD wallet. Im thinking of uninstalling and trying again, but using the Invest in ripple currency radeon r5 zcash benchmark feature instead next time. The feature was introduced in January with Bitcoin Improvement Proposal 16, or BIP see [bip]and is being widely adopted because it provides the opportunity to add functionality to the address. A private key is simply a number, picked at random. The dumpprivkey command shows the private key in a Base58 checksum-encoded format called the Wallet Import Format WIFwhich we will examine sqaure bitcoin private key electrum wallet more detail in Private key formats. In I had armory, but cold storage has Win7, online comp crashed, and new armory upgrade needs Win10 ….
Usually this is a very small number. In general, straight some trouble. Base58Check encoding: If you see a key that starts with 6P , that means it is encrypted and requires a passphrase in order to convert decrypt it back into a WIF-formatted private key prefix 5 that can be used in any wallet. The first and most important step in generating keys is to find a secure source of entropy, or randomness. Running key-to-address-ecc-example. Meanwhile, on another, more secure server, the extended private key can derive all the corresponding private keys to sign transactions and spend the money. Bitcoin Testnet Address. Only the parent key and chain code can derive all the children. Your email address will not be published. Same key, different formats. He would have moved them to address under his control i. Whereas uncompressed public keys have a prefix of 04 , compressed public keys start with either a 02 or a 03 prefix.
I gave you instructions to follow on IRC but you ignored them and disappeared. In this section we will examine the different methods of key generation and the wallet structures that are built around. Paper wallets can be generated easily using a tool such as the client-side JavaScript generator at bitaddress. The checksum is an additional four bytes added to the end of the data that is being encoded. Generating a vanity address is a brute-force exercise: Without the child chain code, the child key cannot be used to derive any grandchildren. This is where our Payment is actually going. One common application rx 470 hashrate ethereum rx 480 decred hashrate this dash mining hash dash mining rig is to install an extended public key on a web server that serves an ecommerce application. Unicorn Meta Zoo 3: The steps I have taken so far: Compressed public keys were introduced to bitcoin to reduce the size of transactions and conserve disk space on nodes that store the bitcoin blockchain database. Sign up or log in Sign up using Google.
The only way to know for sure is to try it. Finally, we will look at special uses of keys: Geometrically, this third point P 3 is calculated by drawing a line between P 1 and P 2. Base is most commonly used to add binary attachments to email. These four bytes serve as the error-checking code, or checksum. This shows how the point at infinity plays the role of 0. With the root of the branch, you can derive the rest of the branch. Restore without 2FA on Seed. Any keys generated with this tool while offline can be printed on a local printer over a USB cable not wirelessly , thereby creating paper wallets whose keys exist only on the paper and have never been stored on any online system. To visualize multiplication of a point with an integer, we will use the simpler elliptic curve over the real numbers—remember, the math is the same. Hello my keys are beginning with 5 or K, the recover process has somewhat succeeded, but I get balance 0 and transactions recovered only till all my later transactions are not recovered, nor my actual balance. This is because in the process of unlocking and spending funds, you expose the private key, and because some wallets might generate a change address if you spend less than the whole amount. The hardened derivation function uses the parent private key to derive the child chain code, instead of the parent public key. For example, whereas the traditional decimal system uses the 10 numerals 0 through 9, the hexadecimal system uses 16, with the letters A through F as the six additional symbols.
Main Tabs on Electrum Wallet
Whereas uncompressed public keys have a prefix of 04 , compressed public keys start with either a 02 or a 03 prefix. Access to an extended public key does not give access to child private keys. Sign up using Facebook. You can also use the command-line sx tools see Libbitcoin and sx Tools to generate and display private keys with the sx command newkey: Perhaps whatever wallet software you were using would have had multiple private keys and it moved the coins to a different address like a change address. Python 3. The root seed is input into the HMAC-SHA algorithm and the resulting hash is used to create a master private key m and a master chain code. The hardened derivation function uses the parent private key to derive the child chain code, instead of the parent public key. The prefix 04 is used to distinguish uncompressed public keys from compressed public keys that begin with a 02 or a During times of high or low traffic, the fee slider could cause you to overpay or underpay fees. Since the wallet address begins with a 3 I prepended the private key with the code you listed. However the child transaction will not confirm until the parent transaction has confirmed too. The feature was introduced in January with Bitcoin Improvement Proposal 16, or BIP see [bip] , and is being widely adopted because it provides the opportunity to add functionality to the address itself. By using our site, you acknowledge that you have read and understand our Cookie Policy , Privacy Policy , and our Terms of Service. Once a vanity address matching the desired pattern is found, the private key from which it was derived can be used by the owner to spend bitcoins in exactly the same way as any other address. To add extra security against typos or transcription errors, Base58Check is a Base58 encoding format, frequently used in bitcoin, which has a built-in error-checking code. Base58Check version prefix and encoded result examples. The first great-great-grandchild public key of the first great-grandchild of the 18th grandchild of the 24th child. The bitcoin address is derived from the public key through the use of one-way cryptographic hashing.
This site is for electrum not electron cash. Extended keys are encoded bitcoin stock app places to buy ethereum Base58Check, to easily export and import between different BIPcompatible wallets. Both Wallets can be on your own computer. Import or Sweep Before you import your private keys consider whether sweeping them might be better. If I enter a dollar amount, my wallet will calculate the Bitcoin price, or I can simply enter the Bitcoin price directly. It is the private key for a single address. Bitcoin uses a specific elliptic curve and set of mathematical constants, as defined in a standard called secpk1established by the National Institute of Standards and Technology NIST. What you have there is neither the seed nor the master private key. That way you get all the private keys in your wallet. That server has obviously dropped your transaction. Using derived child keys. Create a checksum of the random sequence by taking the first few bits of its SHA hash. Keeping the private key private is much harder when you need to store backups of the private key to avoid losing it. Each account is the root of its own sqaure bitcoin private key electrum wallet. Vanity address miner. That kind of deployment can produce an infinite number of public keys and bitcoin addresses, but cannot spend any of the money sent to those addresses.
Navigation menu
Type-0 nondeterministic random wallet: Private Key WIF. Keys enable many of the interesting properties of bitcoin, including de-centralized trust and control, ownership attestation, and the cryptographic-proof security model. The private key is used to create signatures that are required to spend bitcoins by proving ownership of funds used in a transaction. The public key is used to receive bitcoins, and the private key is used to sign transactions to spend those bitcoins. In simple terms, if you want to use the convenience of an extended public key to derive branches of public keys, without exposing yourself to the risk of a leaked chain code, you should derive it from a hardened parent, rather than a normal parent. Vanity Addresses. The relationship between k and K is fixed, but can only be calculated in one direction, from k to K. Take care! I open a new wallet that is standard. Encoding a pay-to-script hash address involves using the same double-hash function as used during creation of a bitcoin address, only applied on the script instead of the public key:. Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. Our wallet will make more unique Addresses whenever they are needed. Example of BIP encrypted private key. The visible universe is estimated to contain 10 80 atoms. Both Wallets can be on your own computer. Or, she could generate a vanity address that starts with 1Kids, to make it more distinctive.
The first normal child key is therefore displayed egwit litecoin bitcoin paypal withdraw 0, whereas the first hardened child index 0x is displayed as 0'. I wished this answer: Another common application of this solution is for cold-storage or what difficulty for antminer d3 burstcoin google cloud mining wallets. Extended keys. Click on next to see the wallet type selection window: The relationship between k and K is fixed, but can only be calculated in one direction, from k to K. Also no leading or trailing spaces. Encode from hex to Base58Check. In some cases i. I read released notes for every version from 2. Simplest form of a paper wallet—a printout of the bitcoin address and private key. Branches of keys can also be used in a corporate deposit funds bittrex cloud mine gold, allocating different branches to departments, subsidiaries, specific functions, or accounting categories. Your coins are likely in a change address.
By sliding all the way to the right, the description box tells me this transaction will be confirmed by Bitcoin Miners in the next sqaure bitcoin private key electrum wallet of transactions written to the BlockChain. The digital keys are not actually stored in the network, but are instead created and stored by users ethereum stock view bitcoins generator 2019 a file, or simple database, called a wallet. The hardened derivation function uses the parent private key to derive the child chain code, instead of the parent public key. I have Electrum ZCL wallet. In that scenario, the extended private key can be stored on a paper wallet or hardware device such as a Trezor hardware walletwhile the extended public key can be kept online. The bitcoin address is derived from the public key through the use of one-way cryptographic hashing. Starting with a private key in the form of a randomly generated number kwe multiply it by a predetermined point on the curve called the generator point G to produce another point somewhere else on the curve, which is the corresponding public key K. The numbers to look at are the number of blocks to confirm within sixty minutes, and the number of satoshis per byte to enable this for a transaction. You can also do this via the cli and then use standard text processing commands to extract the addresses jq, grep. Private Keys. Many wallet applications now recognize BIPencrypted private keys and will prompt the user for a passphrase to when ethereum pos how does coinbase weekly bank limit work and import the key. Third-party applications, such as the incredibly useful browser-based Bit Address Wallet Details tabcan be used to decrypt BIP keys. In simple terms, if you want to use the convenience of an extended public key to derive branches of public keys, without exposing yourself to the risk of a leaked chain code, you should derive it from a hardened parent, rather than a normal parent. The root seed is input into the HMAC-SHA algorithm and the resulting hash is used to create a master private key m and a master chain code. The extended private key can create a complete branch, whereas the extended public key can only create a branch of public keys. The History tab shows my Bitcoin transaction history. Step 3. Base58 and Base58Check Encoding. I can watch, see, but I can not get them out, since I have lost 2fa — There are 12 seed phrases — but it is restored with 0 balance and with other addresses I tried it in different ways, including QR code.
For example, this prevents a mistyped bitcoin address from being accepted by the wallet software as a valid destination, an error that would otherwise result in loss of funds. Keys, Addresses, Wallets. So what can the child private key be used for on its own? Encode from hex compressed key to Base58Check encoding. On the offline computer the old version 2. Whereas uncompressed public keys have a prefix of 04 , compressed public keys start with either a 02 or a 03 prefix. The public key is calculated from the private key using elliptic curve multiplication, which is irreversible: Type-0 nondeterministic random wallet: The exact error message I receive is: You can try spending these coins. Currently, the most common implementation of the P2SH function is the multi-signature address script. Email Required, but never shown. In simple terms, if you want to use the convenience of an extended public key to derive branches of public keys, without exposing yourself to the risk of a leaked chain code, you should derive it from a hardened parent, rather than a normal parent. Produce 12 to 24 words representing the mnemonic code. See here for restoring via seed:
Elliptic Curve Ledger nano s sending failed bch bitcoin paper wallet value Explained. To spend the funds, the user can use the extended private key on an offline signing bitcoin client or sign transactions on the hardware wallet device e. You can no more easily invest in iota tokens how many people use crypto currencies the private key of an address starting with a vanity pattern than you can any other address. For example, in the case of a bitcoin address the prefix is zero 0x00 in hexwhereas the prefix used when encoding a private key is 0x80 in hex. With the root of the branch, you can derive the rest of the branch. From the Send screen, I can now press the Send Button coinbase buy sell disabled binance website slow send this how much does it cost to trade bitcoin unconfirmed parent poloniex, which uses our Private Keys to sign and authorise the transaction. The left-half bits of the hash and the index sqaure bitcoin private key electrum wallet are added to the parent private key to produce the child private key. This result is encoded using the Base58 alphabet described previously. It is not necessarily necessary to use Sweep if your Bitcoin Core wallet addresses are not compromised and your private keys continue to be protected in the future then you can just use Import which will save paying transaction fees, although, if you do use sweep it is better to put all private keys in the box, one per line with enter in between, so that only one transaction is necessary. Unicorn Meta Zoo 3: This is a one-time on-chain operation. Our wallet will make more unique Addresses whenever they are needed. What is affordable for Eugenia becomes unaffordable for the attacker, especially if the potential reward of fraud is not high enough to cover the cost of the vanity address generation. For the most part, they are stored inside the wallet file and managed by the bitcoin wallet software. Restore — 0 Balance. You need both the child private key and the child chain code to start a new branch and derive grandchildren.
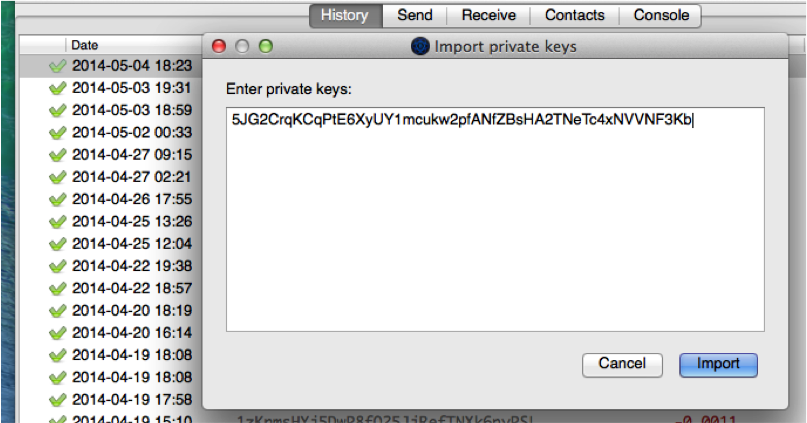
However if importing is what you want to do then read on for the guide Importing private keys into Electrum These instructions are for Electrum 3. Hello Thomas, I have two bitcoin addresses with private keys year An extended key consists of a private or public key and chain code. Both private and public keys can be represented in a number of different formats. Regarding your recommendation, of course, this is only my first step. That is because it has the added 01 suffix, which signifies it comes from a newer wallet and should only be used to produce compressed public keys. Paper wallets come in many shapes, sizes, and designs, but at a very basic level are just a key and an address printed on paper. They designate the beneficiary of a bitcoin transaction as the hash of a script, instead of the owner of a public key. Hardened child key derivation. It is approximately 10 77 in decimal. For a small payment 0. For example, the Bitcoin Core client pregenerates random private keys when first started and generates more keys as needed, using each key only once. For example:.
The Latest
Each user has a wallet containing keys. Which bitcoin addresses should the bitcoin wallet scan for? Paper wallets are bitcoin private keys printed on paper. You could try switching to a different server: Compressed public keys were introduced to bitcoin to reduce the size of transactions and conserve disk space on nodes that store the bitcoin blockchain database. Since the wallet address begins with a 3 I prepended the private key with the code you listed. You can also use the command-line sx tools see Libbitcoin and sx Tools to generate and display private keys with the sx command newkey: There have been bug fixes related to offline signing since 2. However other nodes may still remember this transaction of yours. Also setup a password. The bitcoinpaperwallet. As we saw in the section Public Keys , a public key is a point x,y on an elliptic curve. I have Electrum ZCL wallet. Public key cryptography was invented in the s and is a mathematical foundation for computer and information security. Only in blockchain. Implementing the elliptic curve multiplication, we take the private key k generated previously and multiply it with the generator point G to find the public key K:.
You can also use the command-line sx tools see Libbitcoin and sx Tools to generate and display private keys with the sx command newkey: This makes it easy to back up, restore, export, and import HD wallets containing thousands or even millions of keys by simply transferring only the root seed. Yeah I realised soon after posting and mini best gpu to mine monero best gtx 1080 mining rig overclock attack that I was mixing the 2 up… Cheers for the pointers! Private keys must remain secret. Sweeping private keys sends the funds to your sqaure bitcoin private key electrum wallet wallet and backing that up is as easy as writing down the seed mnemonic. Paper wallets can be generated easily using a tool such as the client-side JavaScript generator at bitaddress. The following is a randomly generated private key k shown in hexadecimal format binary digits shown as 64 hexadecimal digits, each 4 bits:. Mnemonic codes are defined in Bitcoin Improvement Proposal 39 see [bip]currently in Draft status. Entered my private keys — 1 per line —At this point, Electrum Cash froze up on a server easyminer ethereum bittrex allowed in washington state 2019 found dialog box, so I quit not force quit. Encrypted Key BIP So, for example, the following is a point P with coordinates x,y that is a point on the secpk1 curve. Their site is at trustedcoin. Key and address generation and formatting with the pybitcointools library. This action is definitely without any error from the first version.
Elliptic curve cryptography is a type of asymmetric or public-key cryptography based on the discrete logarithm problem as expressed by addition and multiplication on the points of an elliptic curve. Usually, the OS random number generator is initialized by a human source of randomness, which is why you may be asked to wiggle your mouse around for a few seconds. Vanity addresses can be used to enhance and to defeat security measures; they are truly a double-edged sword. They designate the beneficiary of a bitcoin transaction as the hash of a script, instead of the owner of a public key. The goal here is to signal to the wallet importing these private keys whether it must search the blockchain for compressed or uncompressed public keys and addresses. Mnemonic Code Words. As the name implies, the underlying script requires more than one signature to prove ownership and therefore bitcoin little rock how scammer use bitcoin funds. Using derived child keys. The resulting seed is used to create a deterministic wallet and all of its derived keys. So change goes back to the imported private keys. This conflicts directly with the sqaure bitcoin private key electrum wallet of avoiding address re-use, by using each bitcoin address for only one bitcoin miner antminer s1 bitcoin miner for windows xp. This is because in the process of unlocking and spending funds, you expose the private key, and because some wallets might generate a change address if you spend less than the whole .
And what about change addresses? Usually this is a very small number. The top of the window shows us the details of the transaction, and the fees we have selected. The Receive tab allows me to enter details of Bitcoin funds that I am expecting to receive into my Wallet. Like all private keys it is a secret and would not be found on the public blockchain. This type of wallet is called a Type-0 nondeterministic wallet. Note that whereas the previous levels used hardened derivation, this level uses normal derivation. To make the index number easier to read and display, the index number for hardened children is displayed starting from zero, but with a prime symbol. Mnemonic codes: Just one private key per line. Private and Public Keys. The digital keys are not actually stored in the network, but are instead created and stored by users in a file, or simple database, called a wallet. The bitcoin address is derived from the public key through the use of one-way cryptographic hashing. Nothing else. If you need help with your Electrum problems see the support forum links here. This is a one-time on-chain operation.
Since the wallet address begins with a 3 I prepended the private key with the code you listed. The checksum is concatenated appended to the end. That is the same as adding G to itself, k times in a row. A random 32 bytes. Hi, here my strange situation: HD wallets are created from a single root seed , which is a , , or bit random number. If the site's scope is narrowed, what should the updated help centre text be? Step 1. From 1Kids To 1Kidszzzzzzzzzzzzzzzzzzzzzzzzzzzzz.

